The automotive industry is experiencing a surge in BEC and VEC attacks due to its high-value transactions, which involve attacking target employees to steal money or sensitive information by impersonating trusted individuals.
BEC attacks can compromise legitimate email accounts (e.g., CEO), while VEC attacks impersonate vendors an organization works with.
An alarming example is the $37 million loss suffered by Toyota Boshoku when an employee was tricked into changing bank account information for a wire transfer, which highlights the financial and reputational risks these attacks pose to the automotive industry.
Threat actors are targeting the automotive industry with a surge in BEC and VEC attacks, which is likely because the industry commonly deals with high-value transactions and has complex supply chains with numerous vendors.
These factors create an environment with ample opportunities for impersonation and exploitation, as BEC attacks against automotive businesses skyrocketed by 70.5% between September 2023 and February 2024, translating to a significant rise in attack frequency.
According to this pattern, the automotive industry is likely to continue to be a primary target for fraudulent activities involving BEC and VEC.
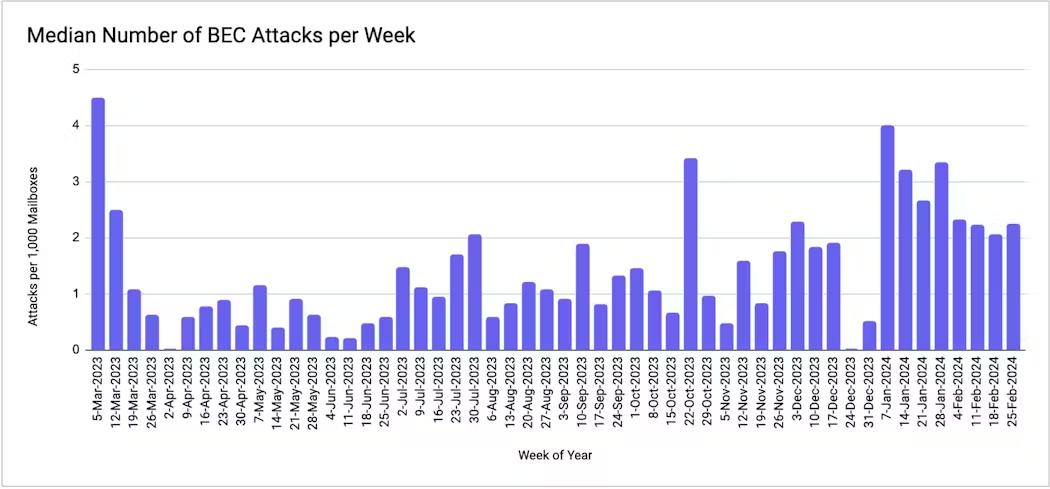
A recent study by Abnormal Security shows a significant rise in Vendor Email Compromise (VEC) attacks targeting the automotive industry, as between September 2023 and February 2024, 63% of automotive organizations experienced a VEC attack, exceeding other sectors like energy/infrastructure, hospitality, and finance.
These attacks use social engineering tactics to bypass email security systems and exploit employees, the weakest link in cybersecurity. Attackers impersonate trusted colleagues or vendors to trick employees into disclosing sensitive information or initiating unauthorized financial transactions, potentially resulting in substantial financial losses.
A business email compromise (BEC) attack targeted a truck dealership’s accounts payable department, where the attacker spoofed the president’s email address and display name to send a fraudulent invoice with a payment request.
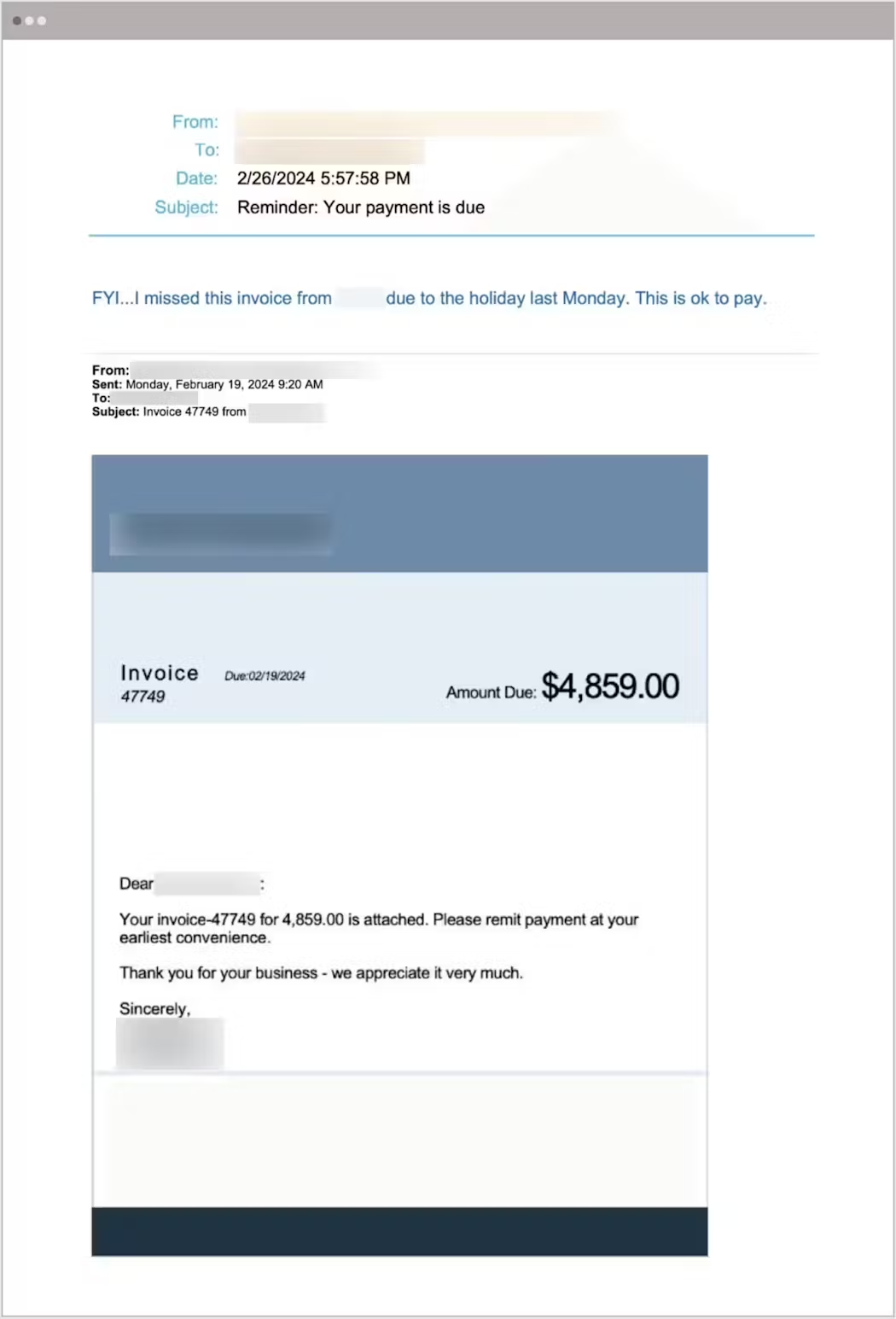
The attack was able to circumvent the legacy email security system because it did not contain any malicious software or links, and it originated from a domain that was trusted.
The impersonation and social engineering techniques, like referencing a real business, further increased the legitimacy of the email, making it difficult to detect and highlighting the need for advanced security solutions to defend against sophisticated BEC attacks.
Automotive companies are increasingly targeted by email attacks that manipulate human vulnerabilities, as traditional security measures like email gateways fail to stop these socially engineered threats as they lack the ability to identify emails that rely on deception instead of malicious links or attachments.
Never forget to check out our YouTube channel,ETHICAL EMPIRE, and keep reading our excitingblogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!