In a collaborative effort, the UK’s Metropolitan Police Service, along with international law enforcement and industry partners, dismantled LabHost, a Phishing-as-a-Service (PhaaS) provider.
The takedown coincided with arrests of individuals involved in the operation, where LabHost offered tools for cybercriminals to build phishing websites, steal login credentials, and bypass security measures, impacting a significant number of victims.
LabHost, a PhaaS platform that emerged in late 2021, offered a suite of tools for cybercriminals to conduct phishing attacks and provided pre-built phishing pages targeting various organizations, including banks, along with customizable templates for credential harvesting.
It facilitated bypassing two-factor authentication (2FA) through Adversary-in-the-Middle (AitM) techniques and included the SMS smishing tool LabSend for phishing message distribution and a management panel to monitor campaign success and stolen credentials.
The ease of use, with features like bespoke phishing page creation and automated deployment, attracted over 2,000 criminals who deployed over 40,000 phishing sites before the platform’s takedown.
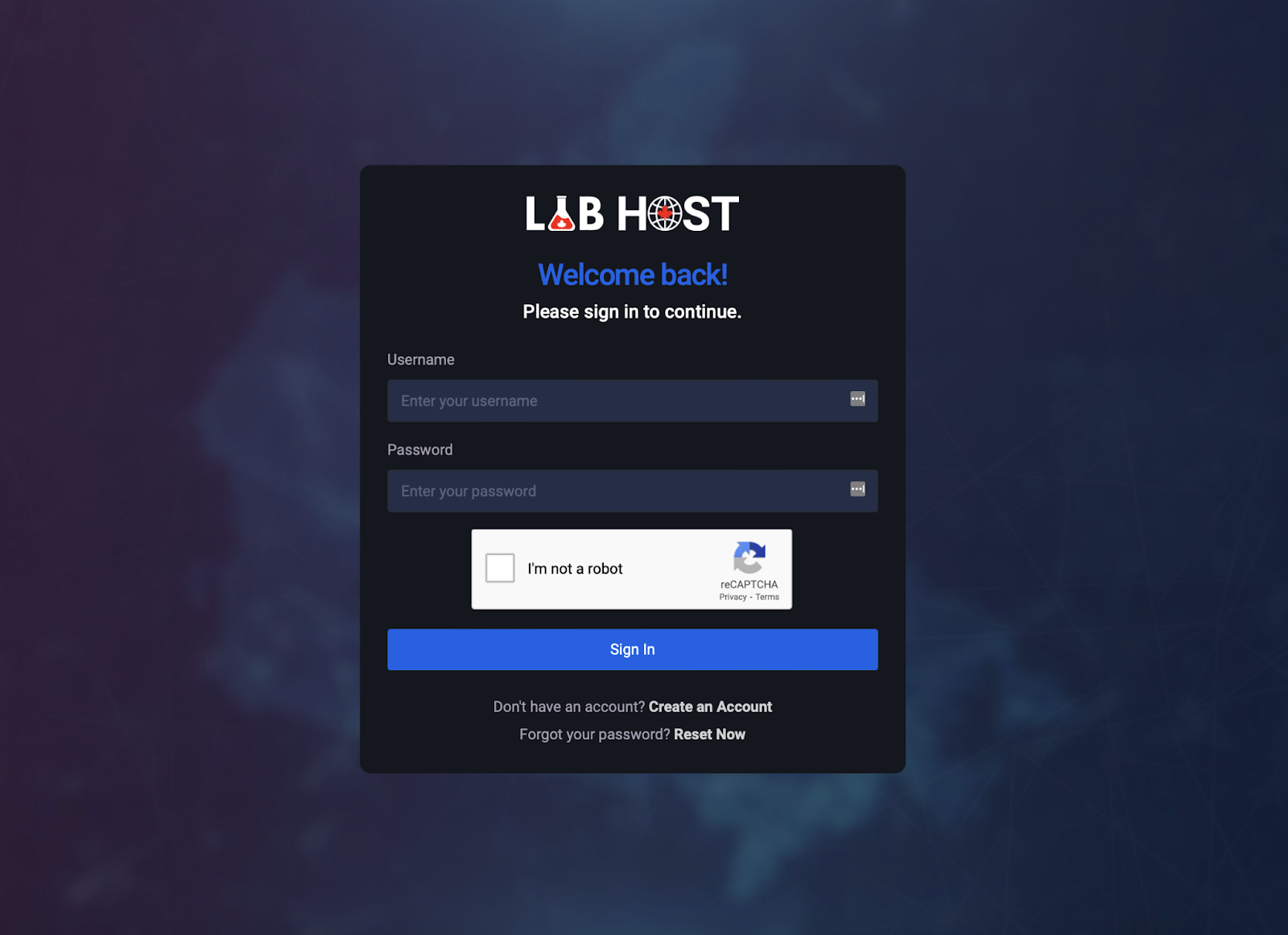
Phishing-as-a-Service (PhaaS) platforms like LabHost lower the barrier to entry for phishing attacks by offering pre-built phishing pages, hosting infrastructure, and email campaign tools.
LabHost, one of the most popular PhaaS providers, offered tiered memberships with features like dozens of phishing pages targeting specific regions (e.g., Canada, US), the ability to host active phishing sites (capped at 3–20 depending on tier), and even international coverage. These memberships were paid via cryptocurrency and included technical support.
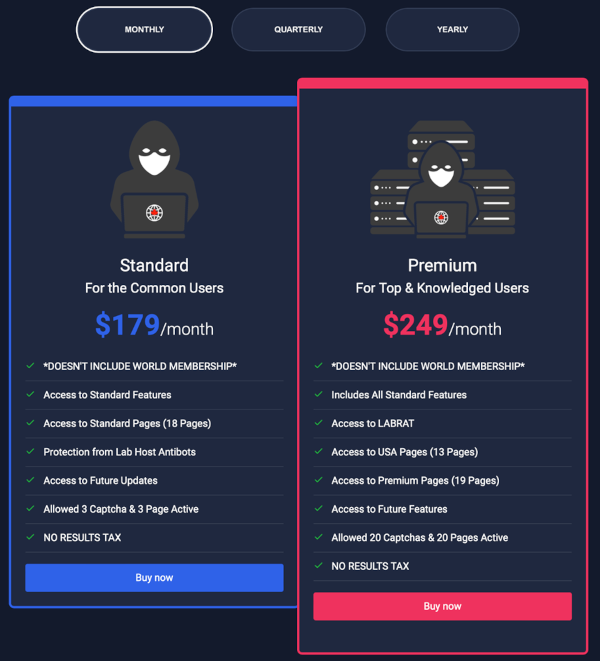
Example attack flow:
LabHost, a now-defunct phishing-as-a-service platform, used SMS phishing against targets in various regions, where the attack mimicked legitimate services like customs charges, prompting users to click a link.
The link led to a fake webpage resembling a trusted brand, such as the Irish postal service An Post, and collected user information in stages, including name, address, and credit card details.
The stolen data was then sent back to LabHost’s central platform for cybercriminals to access, where the attack exploited mobile users’ lack of security software and their tendency to make small mobile transactions without caution.
Law enforcement collaborated internationally to disrupt LabHost, a phishing-as-a-service operation, as they seized LabHost’s infrastructure and associated fraudulent sites, arrested key users, and warned hundreds more.
This takedown targeted not only the service itself but also its criminal user base. The investigation, which Trend Micro assisted in, involved infrastructure analysis, phishing page identification, user classification, and investigations of high-value targets, which is expected to significantly reduce phishing attacks enabled by LabHost.
Trend Micro collaborated with law enforcement to take down LabHost, a service that provided infrastructure for phishing attacks as LabHost offered landing pages (labhost.cc, labhost.co, labhost.xyz, labhost.ru, and lab-host.ru) that were used to generate over 40,000 fraudulent websites.
The takedown disrupts the phishing ecosystem by removing a major provider of tools and creating uncertainty among cybercriminals who relied on LabHost.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!