Cyber Threat Intelligence (CTI) is a process that actively gathers and analyzes information on potential cyber threats by going beyond just collecting data like Indicators of Compromise (IOCs) and Tactics, Techniques, and Procedures (TTPs) used by attackers.
The ultimate goal is to proactively understand the system’s vulnerabilities by analyzing threat actor motivations and capabilities, which are then used to patch vulnerabilities and prevent attacks.
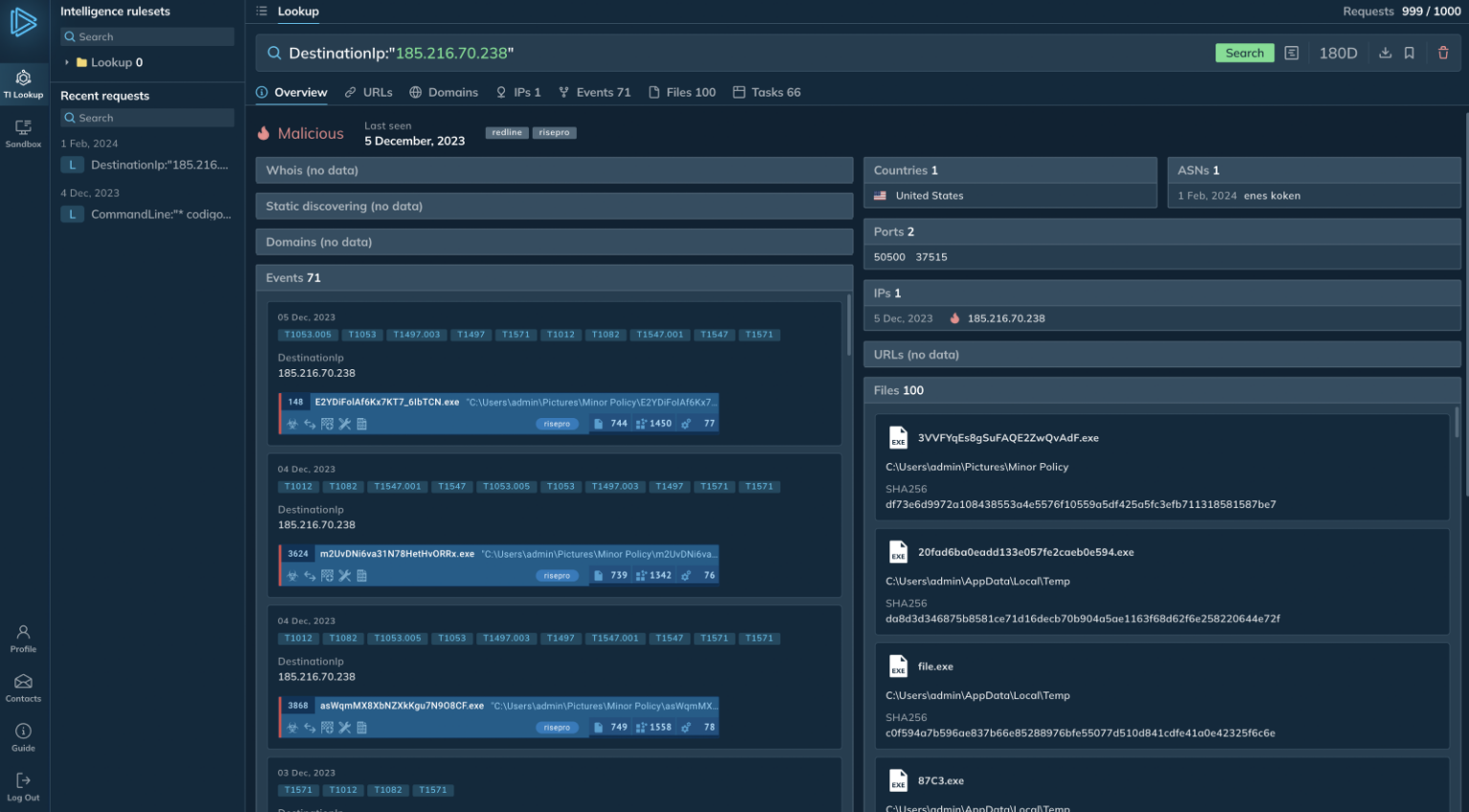
4 categories of Threat Intelligence:
Threat intelligence can be categorized into four categories based on its technical focus and analysis scope. Strategic intelligence provides a high-level view, analyzing threat actor trends and motivations to identify potential attackers.
Operational intelligence focuses on Tactics, Techniques, and Procedures (TTPs) used in attacks, helping in threat detection and response, while Technical intelligence drills down to Indicators of Compromise (IOCs) like IP addresses and file hashes, allowing security systems to block or identify attacks.
Tactical intelligence delivers real-time information for ongoing incidents, including exploited vulnerabilities and specific malware involved. By understanding these categories and using the appropriate tools like threat landscape reports, malware analysis tools, and vulnerability databases, organizations can effectively defend against cyber threats.
Threat Intelligence Life Cycle:
According to AnyRUN, the Threat Intelligence Lifecycle is a 6-step, iterative process for proactive cybersecurity, starting with planning by defining critical assets, intelligence needs, and goals.
Data is then collected from various sources like open-source intelligence (OSINT), human intelligence (HUMINT), and security logs, which are normalized, de-duplicated, and enriched for analysis using techniques like data mining and machine learning.
Insights are then disseminated as reports and alerts to stakeholders, and their feedback is used to continuously refine intelligence requirements, security posture, and the overall effectiveness of the cycle.
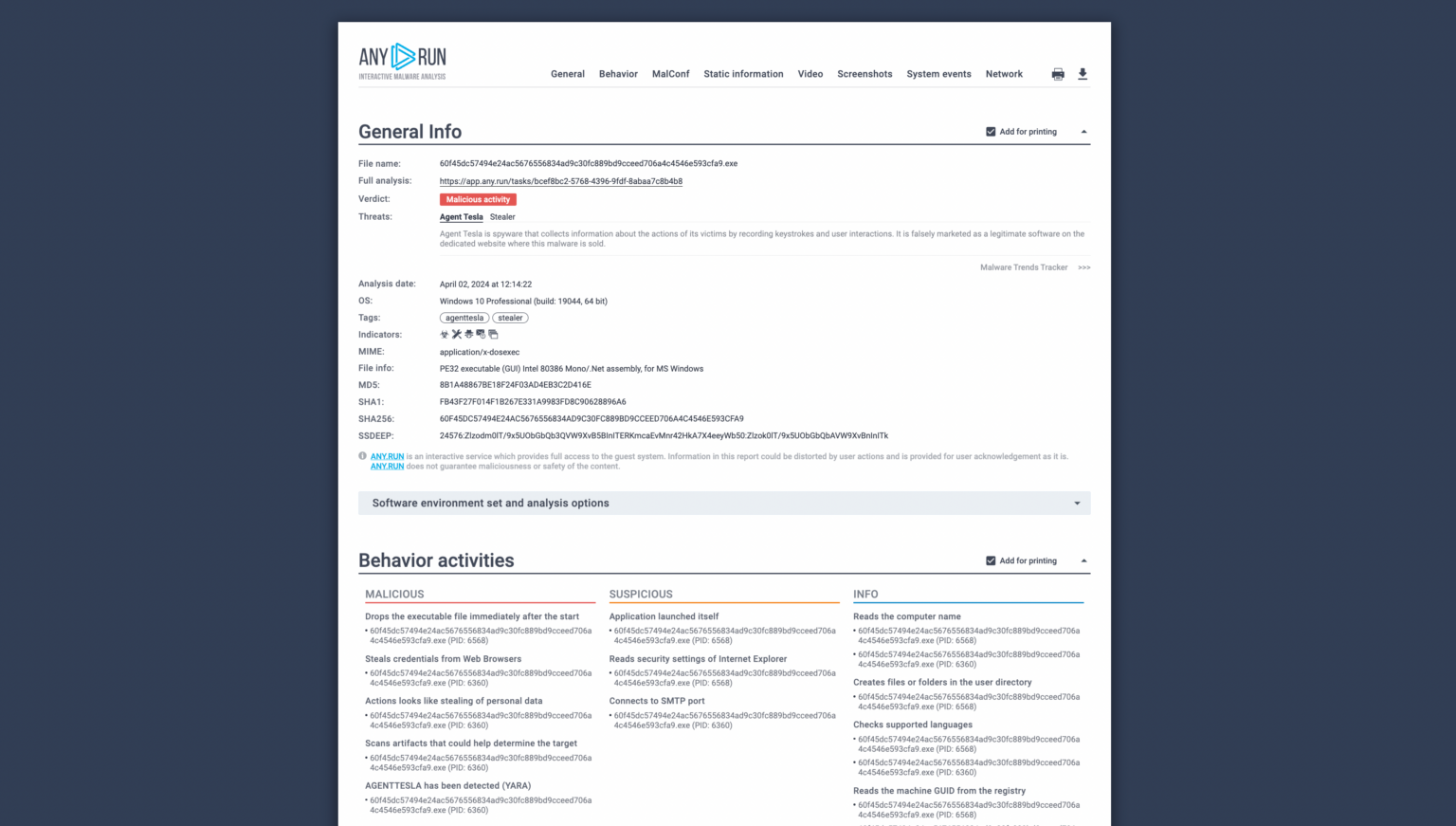
The threat intelligence lifecycle should be completed regularly to maintain relevant information. A full cycle, encompassing planning, collection, analysis, dissemination, and feedback, is recommended every 1-3 months.
Quarterly reviews ensure requirements stay up-to-date while critical intelligence is distributed immediately. Automated threat intelligence feeds gather data continuously, keeping analysts informed of the latest indicators of compromise (IOCs) and their real-world context.
This information is sent to threat intelligence platforms (TIP) and security information and event management (SIEM) to be further analyzed and set up for automated security tools such as endpoint detection and response (EDR) and web application firewalls (WAF).
The continuous cycle ensures security teams have the latest threat intelligence to proactively defend against cyberattacks.
Using malware sandbox to analyze threats
Faced with suspicious network logs and an unidentified malicious executable, traditional analysis might not be enough and to rapidly assess the previously unknown threat, an interactive sandbox like ANY.RUN can be utilized.
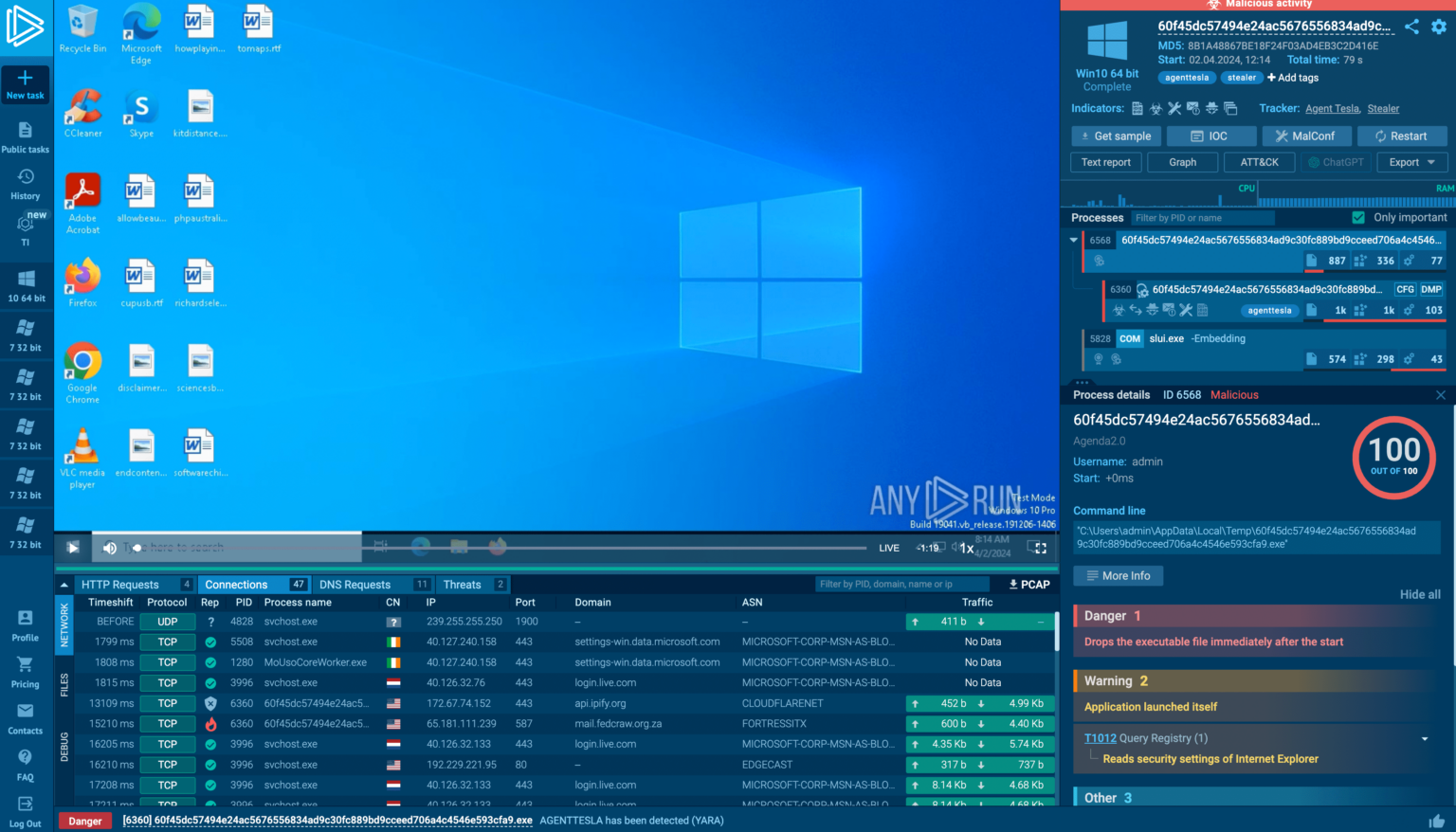
The sandbox mimics a real system, allowing the malware to execute in a controlled environment by actively monitoring and collecting network activity, hard drive modifications, and memory changes during execution, providing real-time insights into the malware’s capabilities.
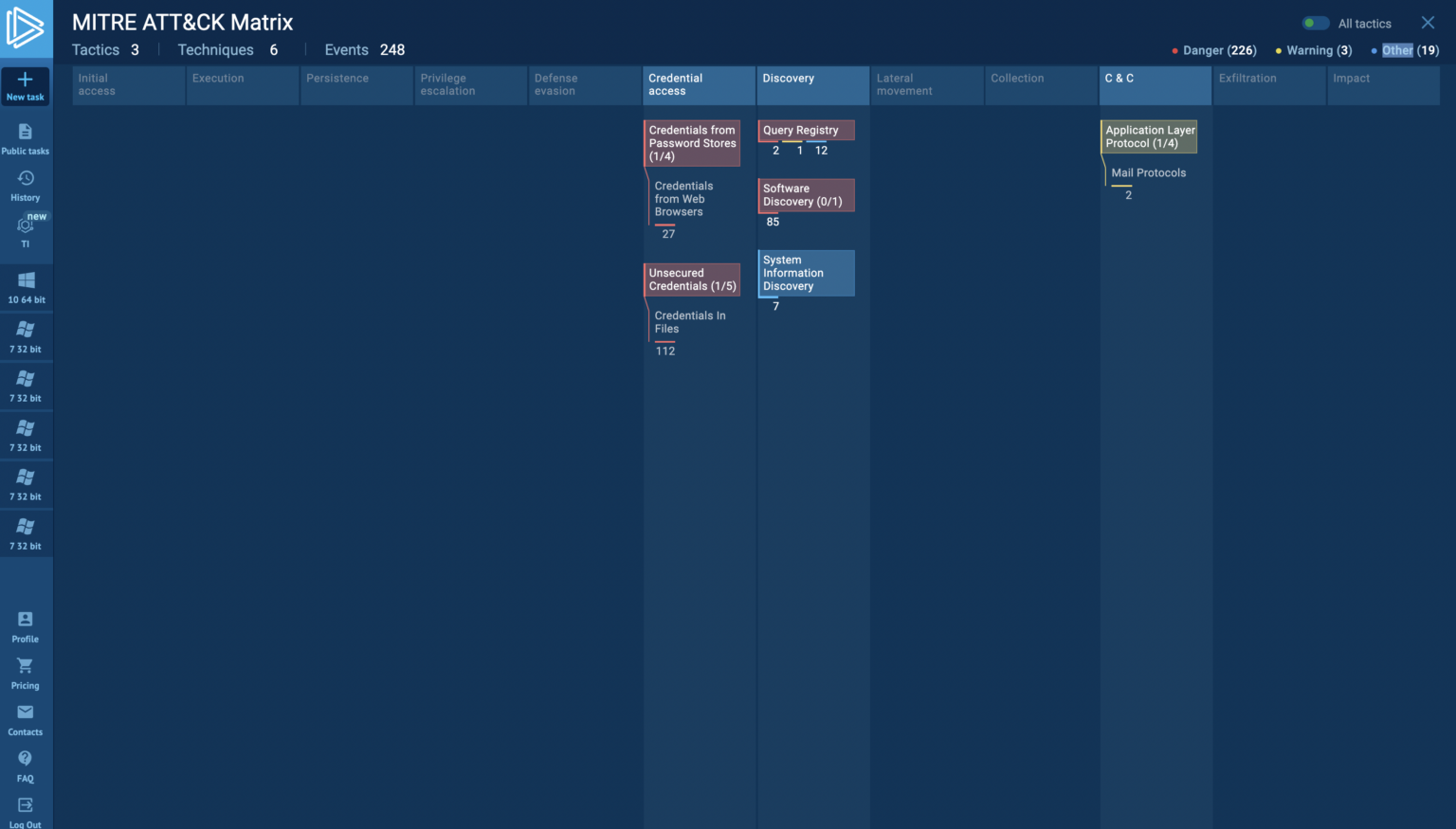
Swift analysis helps security professionals understand the threat’s behavior before taking further action, while security products often offer built-in reporting features to expedite threat intelligence distribution, which can be tailored to specific audiences as reports.
For instance, the MITRE ATT&CK Matrix focuses on immediate sharing, mapping malicious actions to techniques and providing mitigation suggestions, while comprehensive text reports can be generated, allowing for detailed analysis and secure sharing with stakeholders.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!