Who’s Knocking on Your Ports? Unveiling Malware-Driven Vulnerability Scans

Attackers are increasingly using malware-infected devices to scan target networks for vulnerabilities, shifting away from traditional direct scans, which allow them to hide their identity (covering traces), bypass geographical restrictions (bypassing geofencing), and expand their botnets.
Compromised devices provide more resources to launch large-scale scans compared to what attackers could achieve on their own and by analyzing characteristics like high request volume and known threat signatures, security systems can identify both established and novel malware-initiated scanning attempts.
What are scanning attacks?
Attackers use scanning techniques to discover weaknesses in target systems, involving probing ports to identify available services, searching for known vulnerabilities (CVE), and even fingerprinting the operating system.
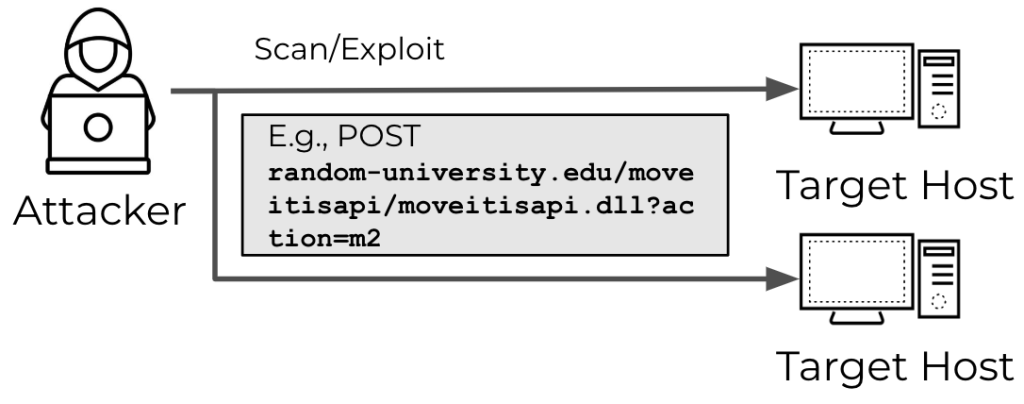
In the illustrated attack model, the attacker sends an HTTP POST request, potentially exploiting a MOVEit vulnerability (CVE-2023-34362) on the target system (random-university.edu) and if the system is vulnerable and lacks protection, the attacker’s scan could lead to a successful compromise.
Attackers target widely used technologies like routers, web application frameworks, and collaboration tools. The data shows a surge in router attacks, with incidents targeting Ubiquiti EdgeRouters and Cisco and NetGear routers, where attacks are not limited to specific brands and attackers are actively scanning for vulnerabilities.

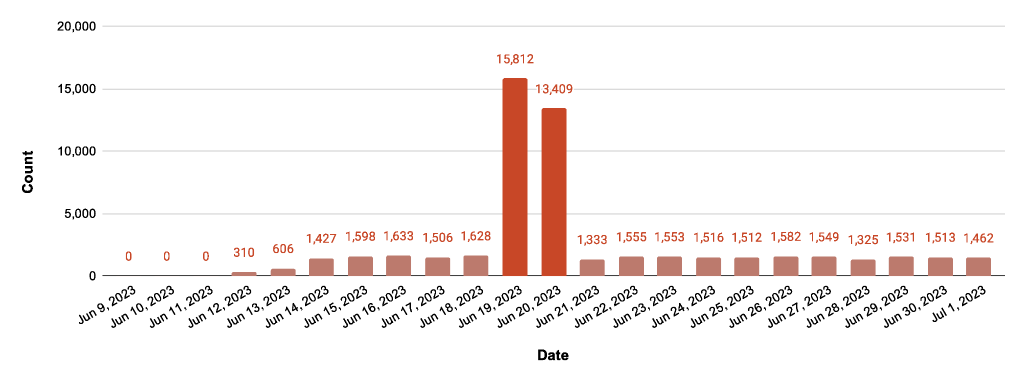
By looking at a lot of requests (7,147 in 2023) to endpoints like “guestaccess.aspx,” which is connected to the MOVEit vulnerability (CVE-2023-34362, released in June 2023), multi-network traffic analysis led to new scanning patterns.
Interestingly, telemetry shows requests to the endpoint even before the official CVE publication date, indicating potential pre-exploit scanning activity and by analyzing traffic data from various networks, it has been identified that over 66 million requests in 2023 could be linked to scanning attempts.
Attackers are hiding malicious URLs within exploit requests, using previously unseen domains for payload delivery and command-and-control (C2) communication to block known malicious URLs.
Research by Palo Alto Networks shows that these scanning attempts with new URLs come before the actual malicious payloads, creating a window of opportunity to block the initial scan and prevent the attack from ever deploying its full arsenal.
Malware was used by attackers to hijack infected devices and launch scanning attacks after contacting a command-and-control (C2) server for guidance, which frequently involves scanning target devices for vulnerabilities.
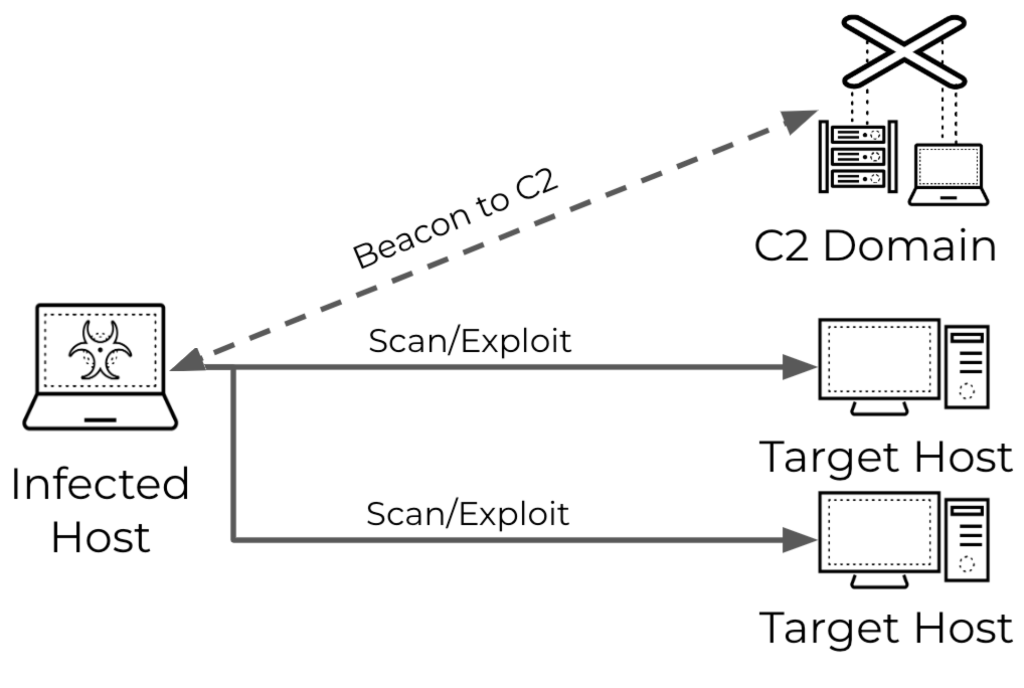
The scans can be targeted at specific entities or broad in scope, depending on the attacker’s goals, allowing attackers to use the resources of compromised machines to automate reconnaissance and potentially exploit discovered vulnerabilities.
The Mirai botnet is constantly evolving to exploit new vulnerabilities; in this case, Mirai targets a Zyxel router’s /bin/zhttpd/ component to download a malicious file for further propagation.
The exploit utilizes an insufficient input validation vulnerability to download a malicious file and then chmod it to 777 permission to execute itself and by monitoring scanning activities across multiple networks, new scanning patterns can be detected more rapidly.
Ivanti Vulnerability Scanning
Researchers identified a surge in scans targeting recently disclosed Ivanti vulnerabilities (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893) exploiting a chained authentication bypass and command injection attack.
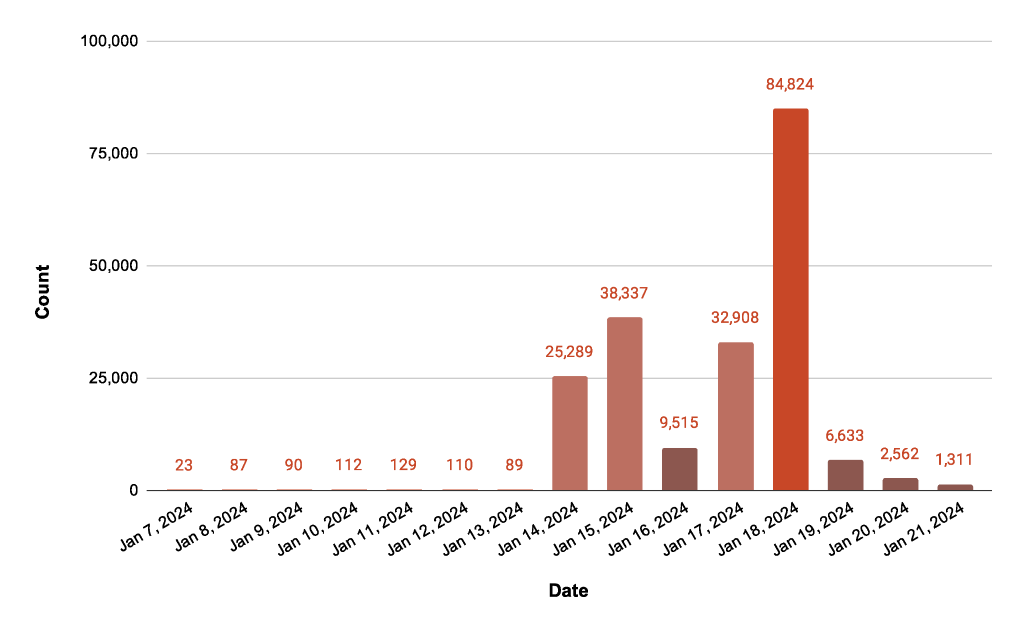
The attackers use a path traversal vulnerability in the `/api/v1/totp/user-backup-code` endpoint to bypass authentication for the `/api/v1/totp/license/keys-status` endpoint, which had a command injection vulnerability.
When vulnerable systems were attacked, it gave attackers the ability to potentially steal information or execute arbitrary commands.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!