A new social engineering campaign (DEV#POPPER) targeting software developers has been identified, which is likely linked to North Korean threat actors and uses fake job interviews to deliver a Python-based Remote Access Trojan (RAT).
Researchers are investigating malicious software repositories used in the attacks to understand how attackers infect systems and their capabilities.
Attackers are targeting software developers with social engineering tactics through fake job interviews and masquerading as legitimate companies as they request candidates download and run malicious Node.js software from seemingly reputable sources like GitHub.
It exploits the developers’ professionalism and trust in the interview process, as refusing the seemingly standard request could jeopardize their job chances. The attackers’ credibility and imitation of real interview procedures lull the targets into a false sense of security, facilitating malware deployment.
Stage 1: Malicious NPM package
The interviewee receives a seemingly legitimate Node.js package containing a backend directory. Hidden within this directory is a JavaScript file, `imageDetails.js`, that appears to use Mongoose for MongoDB interaction.
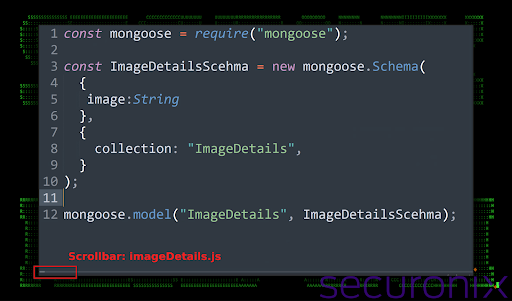
However, a suspiciously long scrollbar hints at obfuscated code and a closer inspection reveals a massive block of obfuscated code hidden beyond the viewable area.
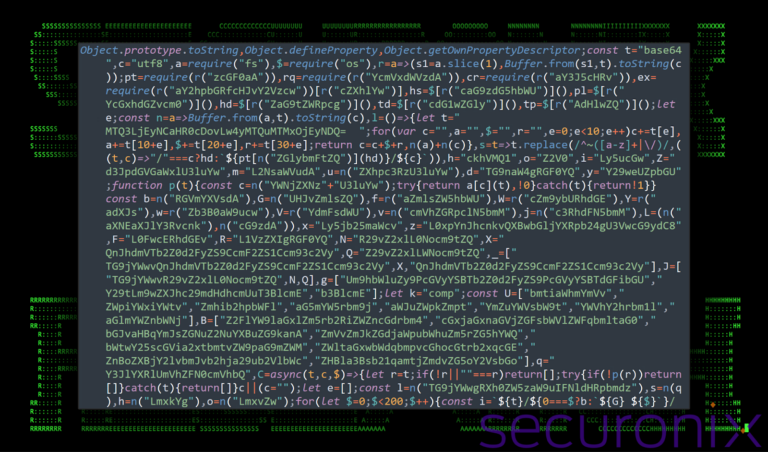
This malicious code, likely extracted for easier analysis, uses multiple layers of obfuscation techniques like base64 encoding and variable substitutions.
Stage 2: Command execution and payload download
The malicious JavaScript code within the compromised NPM package triggers a NodeJS process that executes a series of commands, as first it uses curl to download a compressed file (.zi) from a specified web server.
Next, it extracts the downloaded archive (likely a ZIP file) using the tar command, placing the extracted content in the victim’s user directory, and finally, it executes a hidden Python script (“.npl”), presumably located within the extracted files, by calling python.exe, which will effectively download the second stage payload, extract it locally, and then execute the next malicious stage.
Stage 3: Python code execution (.npl)
A malicious actor utilizes a hidden Python file (“.npl”) containing obfuscated code and employs base64 encoding and XOR operations to conceal the malicious payload, which is then decoded and presumably executed using the `exec()` function.
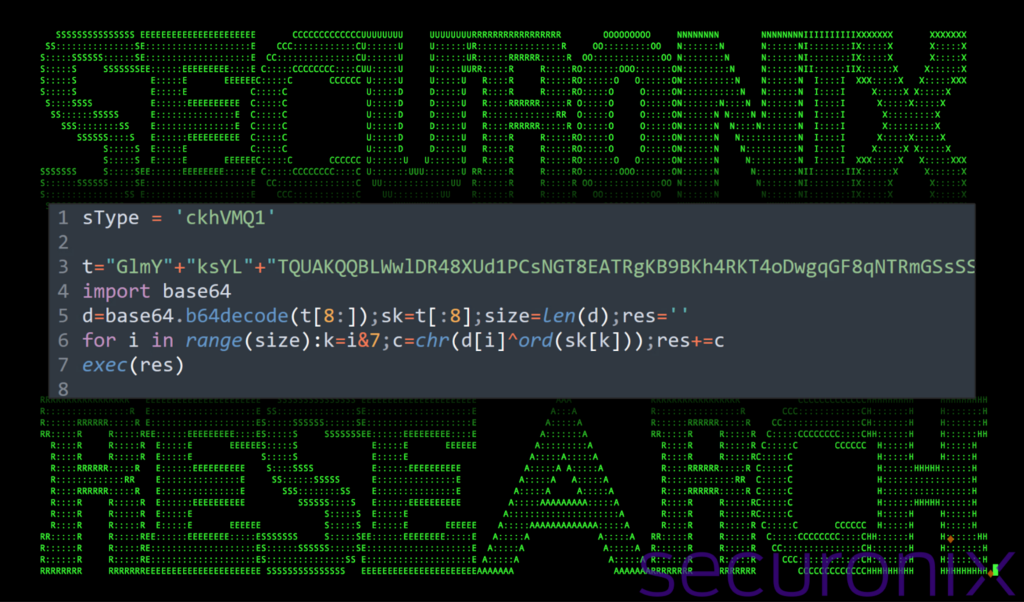
The decoded script gathers its current location, extracts a hardcoded command-and-control (C2) server address and triggers the execution of another Python script located on the compromised system.
Stage 4: Python code execution (pay)
The “pay” Python script, similar to the previous one, decodes a Base64 string containing malicious code, which harvests system and network information from the infected machine, including OS details (type, release version, username), and a unique device identifier created by hashing the MAC address and username. The script then transmits this stolen data to a remote server.
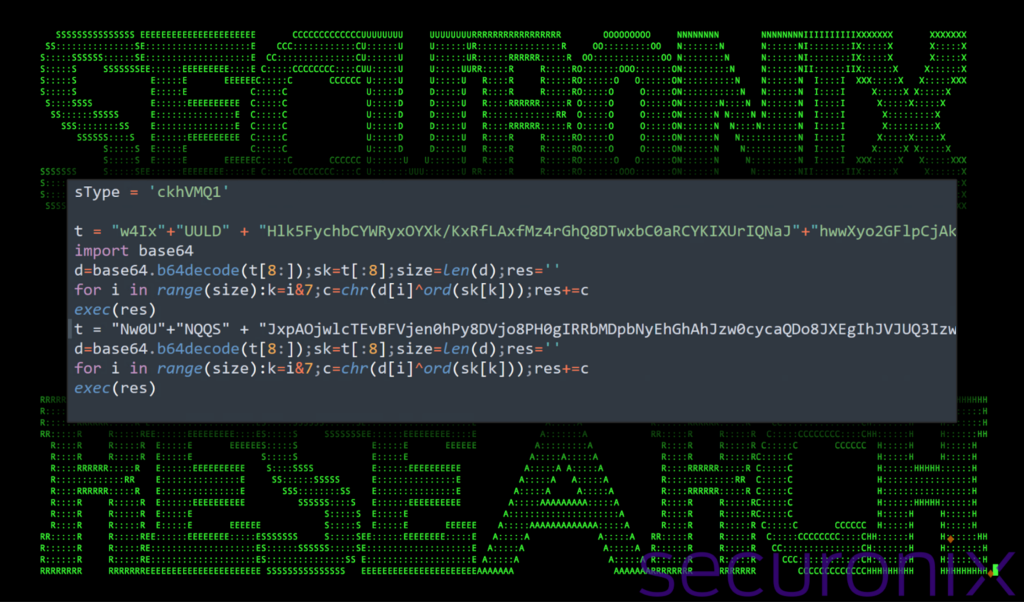
The malicious code extracts sensitive information from the infected device, including OS details, a username, and a unique ID, which is then sent to the attacker’s server in JSON format.
The second code acts like a RAT, granting remote control to the attacker, which includes establishing persistent connections, navigating the file system, filtering and exfiltrating specific files, executing commands, and monitoring user activity through clipboard and keystroke logging.
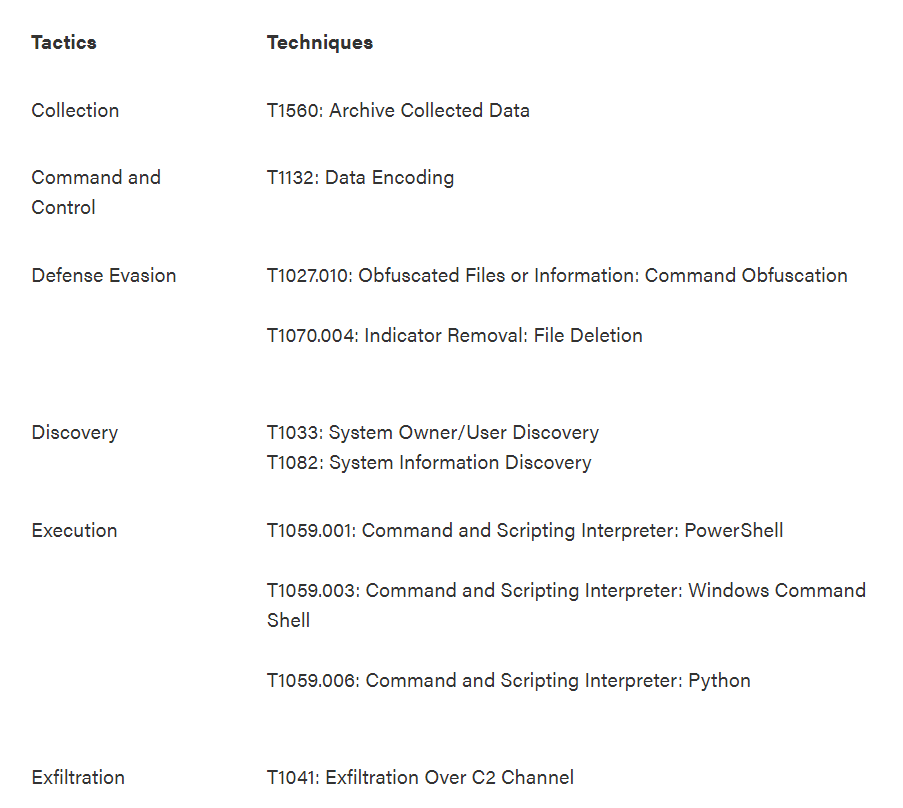
According to Securonix, once the machine has been compromised, the attacker is able to steal data, manipulate files, and maintain persistence on the device.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!