Car vulnerabilities can arise from various sources, including software, hardware, communication channels, and human factors. These vulnerabilities can have severe consequences, potentially causing accidents, theft, or the loss of sensitive information.
Software vulnerabilities: These can include flaws in the code or logic of vehicle control systems, infotainment systems, mobile applications, and other software components.
Hardware vulnerabilities: These affect the physical components of the car, such as sensors, controllers, or communication modules.
Communication vulnerabilities: Modern cars rely on multiple communication channels, both internal (e.g., CAN bus) and external (e.g., wireless technologies).
Attack Surface:
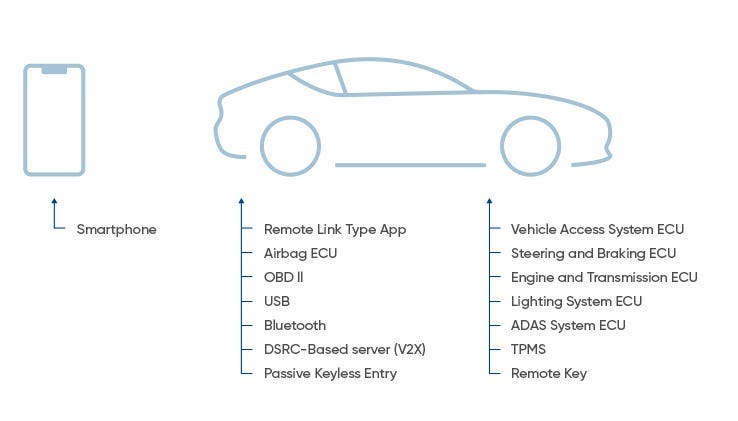
An on-board network of Electronic Control Units (ECUs), which are specialized computers with carefully crafted and personalized software, manages modern vehicles.
Internal communication interfaces, such as diagnosis protocols, external and user-accessible interfaces, including USB sockets, and low-level hardware interfaces make up the majority of the automotive attack surface.
Let’s see some of the common attack types that are being performed or can be used to harm the vehicle.
- Relay Attack
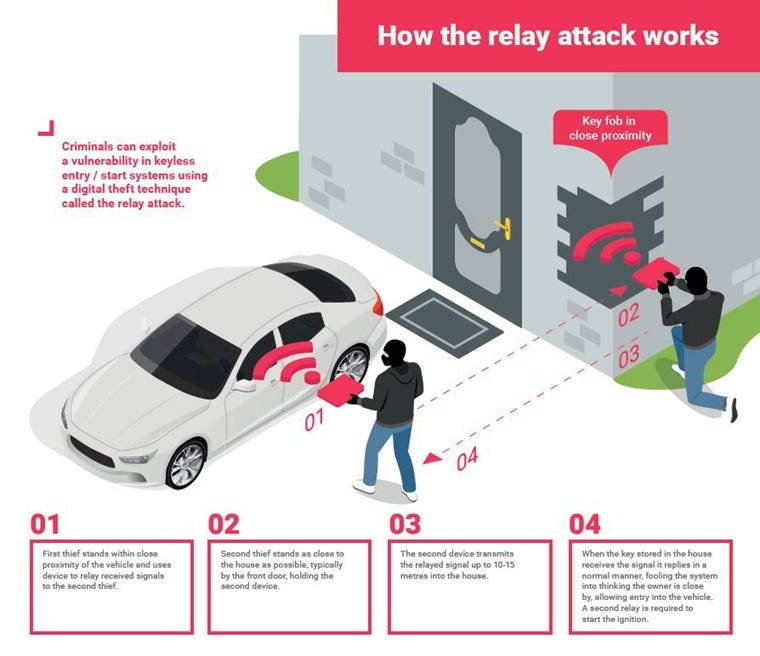
Relay attack is one of the most common attacks in automotive hacking. A replay attack is when a wireless signal, such as a door unlock signal, is recorded, and then played back at a later time with a device like a HackRF SDR.
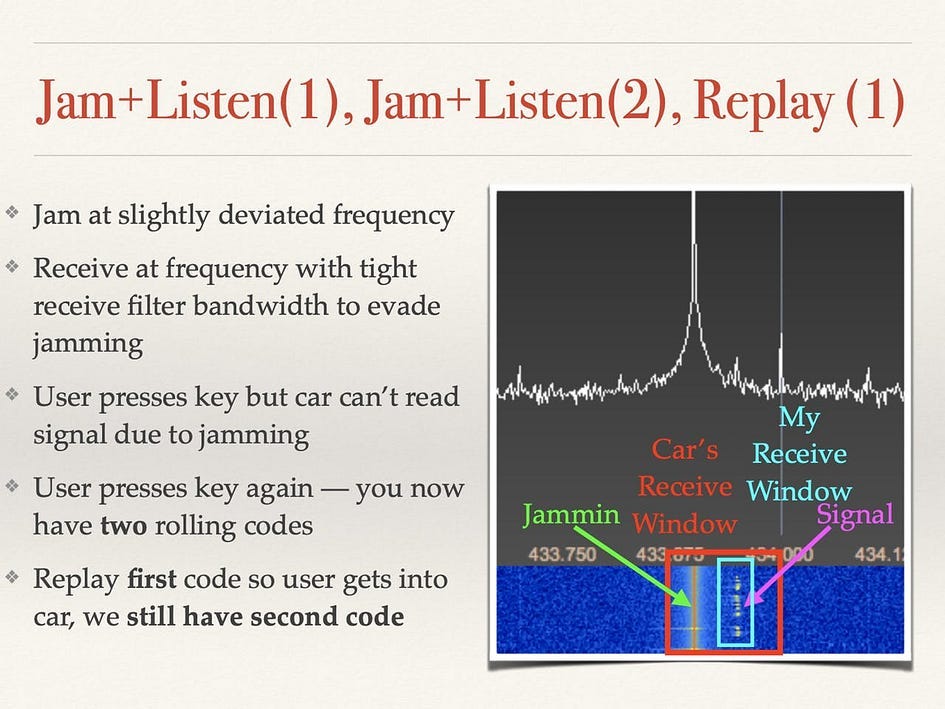
2. Roll-Jam Attack
A rolling code is used to prevent normal relay attacks, but these codes can still be bypassed using an attack known as the Roll-Jam attack. The Roll-Jam attack works by recording and blocking the radio signal from the key fob.
Because the signal is blocked, the car doesn’t unlock, and the owner will naturally try again. That creates a second signal that is also recorded and blocked, but this time the attacker replays the first code to unlock the door, and now the attacker will always have the next code.
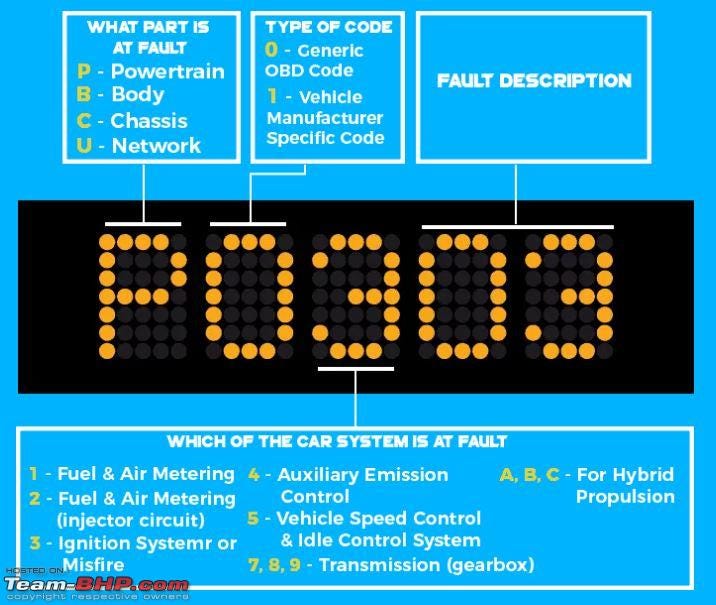
3. Attacking Vehicle’s DTCs
DTC (Diagnostics Trouble Code) is a five-character alphanumeric code. The PCM (Powertrain Control Module) stores fault codes as DTC in different places. When storing the DTCs, the PCM takes snapshots of all the relevant engine components in what is known as freeze frame data, which typically includes information such as the following:
• DTC Involved
• Engine load
• Engine revolutions per minute (RPM)
• Engine temperature
• Fuel trim
• Manifold air pressure/mass air flow (MAP/MAF) values
• Operating mode (open/close loop)
• Throttle position
• Vehicle speed
Eg: P0477 (exhaust pressure control valve low) and U0151 (lost communication with restraint control module).
Attackers may target the freeze frame data and DTCs of a vehicle to cover up illicit activity. For instance, if an exploit only needs to take advantage of a brief, temporary circumstance, it will almost certainly miss the event in a vehicle’s freeze frame data because of recording delays.
When fuzzing a vehicle’s system, an attacker might look for fired DTCs and use the information in a DTC to identify the problematic component. The most likely time for this kind of attack to take place is not during an active exploit but rather during the research stage of an attack (when an attacker is trying to figure out which components the randomly generated packets were affecting).
4. Attacking Wireless Systems
Embedded wireless systems can be easy targets. Due to their small size and specialized functionality, they frequently rely solely on short-range signals for security, and the ECU rarely performs any additional checks to verify the data beyond the CRC algorithm and the signal itself.
These involve attacks on short and long-range wireless communication via Wi-Fi, BLE, NB-IoT, and GSM.
Some of the short-range attacks include WiFi or Bluetooth packet sniffing, MITM, jamming, and protocol-related exploits. Long-range communication includes cellular networks and GPS signals, which may be prone to spoofing, tracking, or stealing sensitive information.
5. Hacking With TPMS
The TPMS (Tire Pressure Monitoring System) is a straightforward gadget that fits inside the tire and communicates with the ECU to send data about tire pressure, wheel rotation, and temperature as well as alerts about certain conditions, such as low sensor batteries.

By installing receivers in the areas you want to track, TPMS can be used to track vehicles. For instance, all you’d need to do to track cars entering a parking garage is set up a few receivers near the entrance and exit points.
Once you have access to the TPMS signal, you can send your own forged packets by setting up GNU Radio as a transmitter instead of as a receiver
In addition to tracking a vehicle, TPMS can be used to start an action, such as opening a garage door when the car approaches or starting a more sinister process.
So these are a few attacking techniques that are being or can be used on cars. There are various other methods that are being exploited and researched. Automotive security is growing rapidly with the advancement of luxuriousness and technologies in connected vehicles, so there’s a huge upcoming demand for automotive cybersecurity specialists.
References:
https://payatu.com/blog/automotive-attacks/
https://evelta.com/blog/introduction-to-automotive-electronics/
https://events19.linuxfoundation.org/wp-content/uploads/2018/07/ALS19-Common-Attacks-Against-Car-Infotainment-Systems.pdf
Car Hacker’s Handbook — Craig Smith
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!
Try Hack Me’s 1 Month Voucher Giveaway Link : https://forms.gle/xpqS2jgspyC22K5d8