Researchers identified a new variant of the Redline Stealer trojan utilizing Lua bytecode for obfuscation and malicious functionalities, which has achieved global reach, infecting users across North and South America, Europe, Asia, and even Australia, as evidenced by McAfee’s telemetry data.
The discovery emphasizes the widespread threat that Redline Stealer poses and the evolving techniques malware authors use to avoid detection.
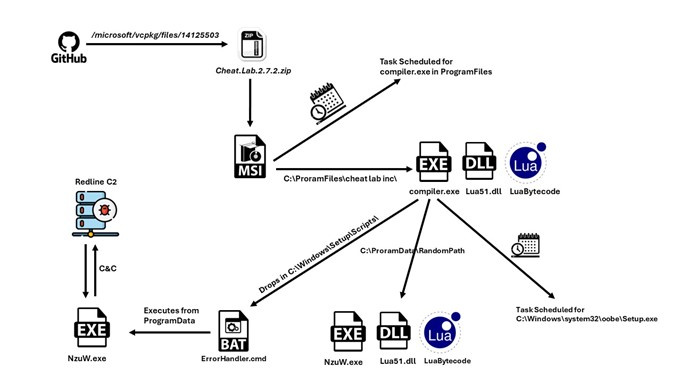
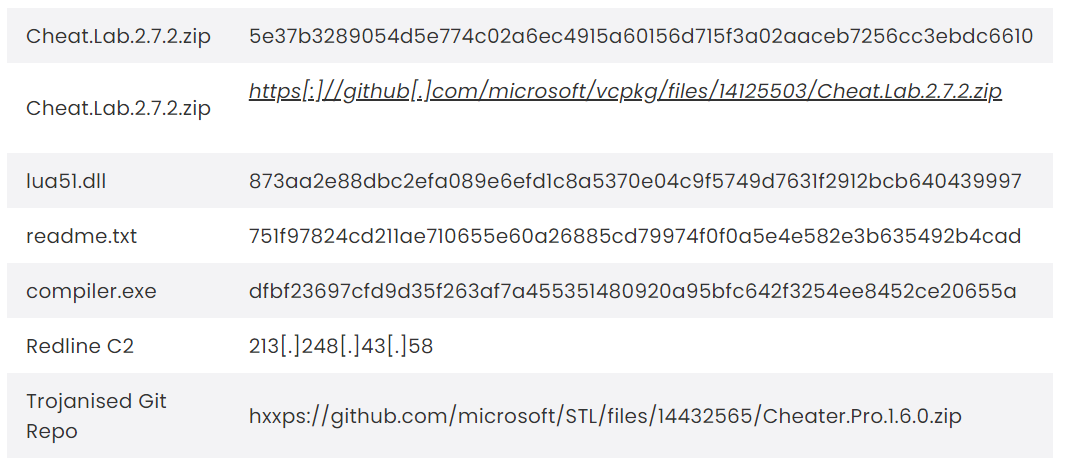
Attackers abused GitHub to host a malicious ZIP file disguised as a game cheat, containing an MSI installer that drops modified Lua files and a text file containing Lua bytecode.
The installer exploits legitimate tools (compiler.exe and lua51.dll) to compile and execute the Lua bytecode at runtime. To ensure persistence, the malware creates scheduled tasks and leverages a legitimate Windows tool (oobe.exe) to trigger a script execution, ultimately running the malicious Lua code, which then retrieves the victim’s IP address.
C2 Communication and stealer activity
An infected machine communicated with a Command and Control (C2) server using HTTP. The C2 server instructed the machine to take screenshots (task ID: OTMsOTYs) and the infected machine responded with a base64-encoded string.
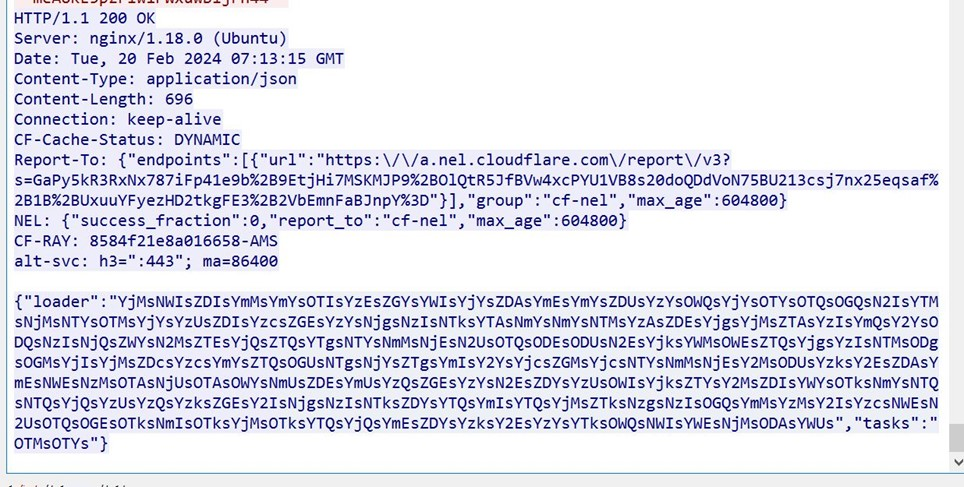
The machine then sent an HTTP PUT request to the C2 server at /loader/screen with the encoded screenshot data.
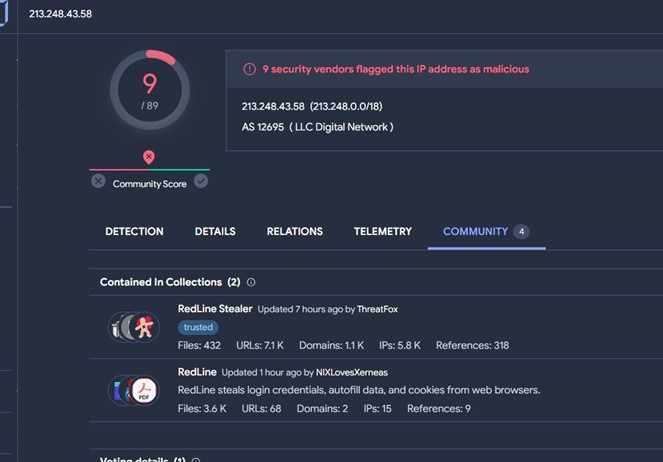
Analysis of the network traffic revealed the C2 server IP belonged to the RedLine malware family, and the user-agent string in the request was “Winter.”. Further inspection confirmed the data sent was a bitmap image file named “Screen.bmp.”.
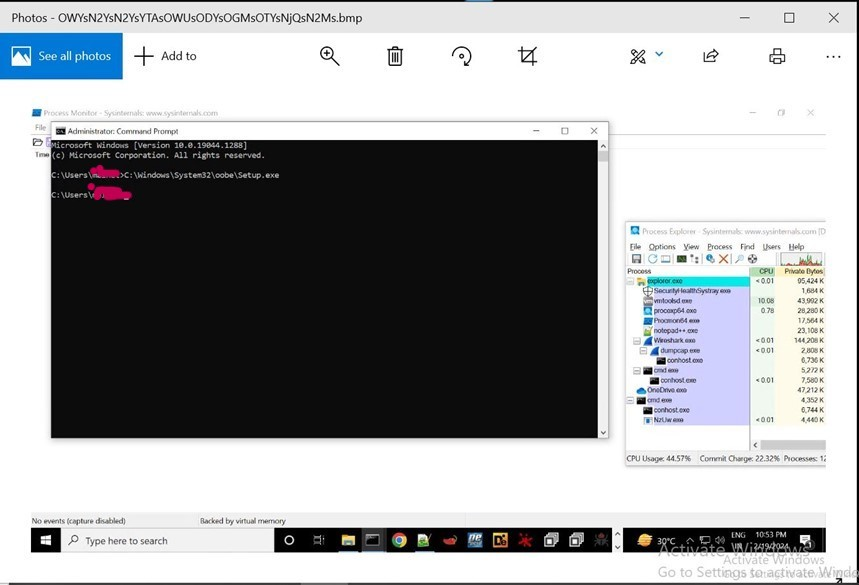
Bytecode File Analysis
McAfee’s analyzed a bytecode file that was difficult to decompile perfectly using various open-source tools, while the resulting Lua script had errors and wouldn’t compile. By making changes based on the errors (sensitization), they were able to compile the script and proceed with debugging.
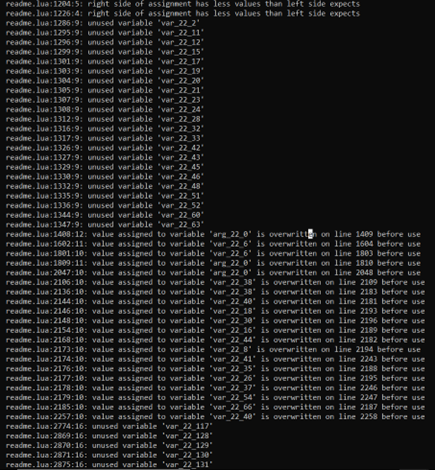
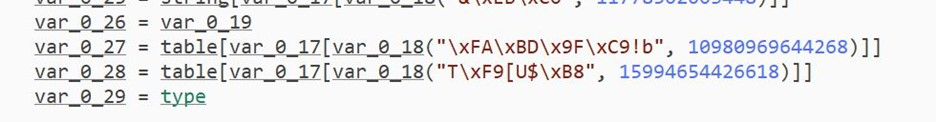
The script appears to involve a two-step decryption process, as first, data is encoded multiple times and stored in a table (var_0_19). Then, a separate table (var_0_20) likely holds the decryption key, and a lengthy loop iterates through the encoded data in var_0_26, potentially containing extraneous lines, and performs the decryption.
Setting a breakpoint at line 1174 allowed to observe the decryption process in action, revealing strings like “Tamper Detected!” within the decrypted data in var_0_26.
The LuaJIT malware analyzed creates a new Lua state, loads the required libraries, and then obfuscates the loaded LuaJIT bytecode by moving a 200-byte section to a random location in memory.
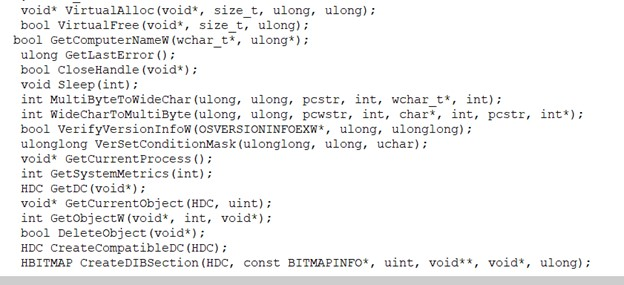
The malware further manipulates table values using floating-point arithmetic and xor instructions, while function definitions for variables and arguments used in the script are identified.
By leveraging the FFI library, the malware creates a mutex, dynamically loads a DLL using LdrLoadDll from ntdll.dll, and retrieves MachineGuid and ComputerName from the Windows registry. Finally, it gathers this information along with other data and transmits it to the C2 server.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!