In a chilling post on a notorious hacking forum, a threat actor, identified as “Cvsp,” has purportedly unveiled a zero-day exploit for Microsoft Outlook, capable of executing remote code execution (RCE) attacks. The exploit, according to Cvsp, has been successfully tested on various versions of Microsoft Office, including Office 2016, Office 2019, Office LTSC 2021, and Microsoft 365 Apps for Enterprise.
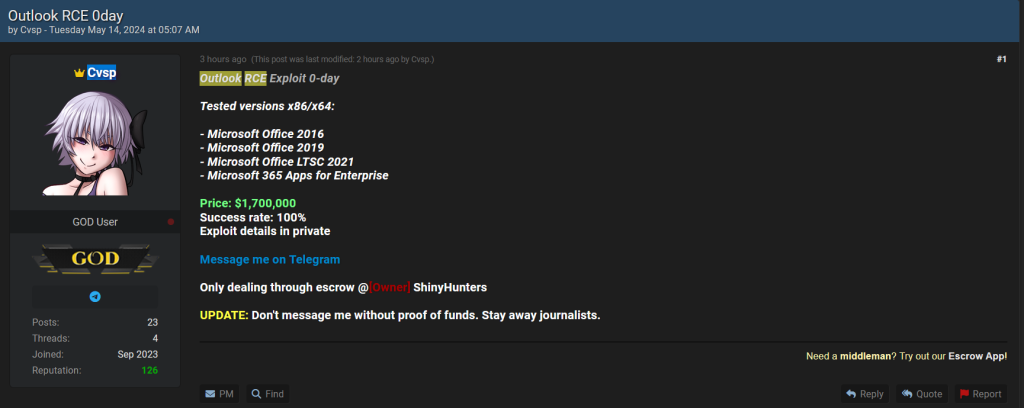
The zero-day exploit, touted to have a 100% success rate, poses a grave threat to millions of users worldwide who rely on Outlook for their email communication and productivity needs.
Cvsp has set a staggering price tag of $1,700,000 for the exploit, claiming to provide detailed exploit specifics exclusively to interested buyers through private communication channels. The threat actor has explicitly stated that all transactions will be conducted through an escrow service, with the handle @ShinyHunters specified as the intermediary.
In an update to the post, Cvsp issued a stark warning, cautioning against contacting them without providing proof of funds and specifically instructing journalists to refrain from reaching out.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!