Hunting Named Pipes with Sysmon
Pipes, a form of inter-process communication (IPC), can be monitored for suspicious activity. Sysmon event codes 17 and 18 can be used to capture pipe creation and connection on endpoints.
There are two types of pipes: anonymous pipes usable within a single host and named pipes usable across networks via SMB or RPC protocols. Network traffic containing named pipe communication can be captured from network wire data for further analysis, which is valuable for security monitoring alongside endpoint data.
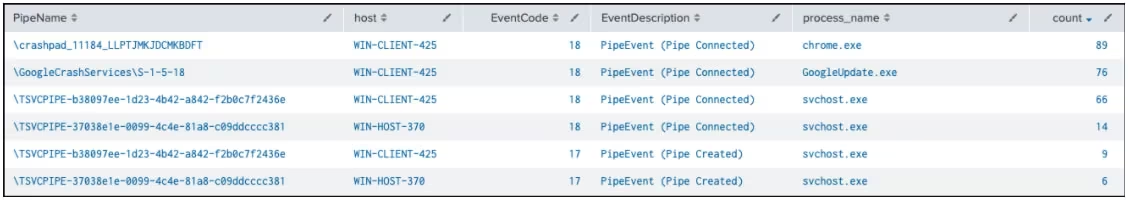
Sysmon data with Event Codes 17 and 18 can reveal named pipe creation and connection events, which return the pipe name, host, event type, event description, and involved process. However, results include frequent events from legitimate applications like Chrome and Google Update, making further investigation necessary.
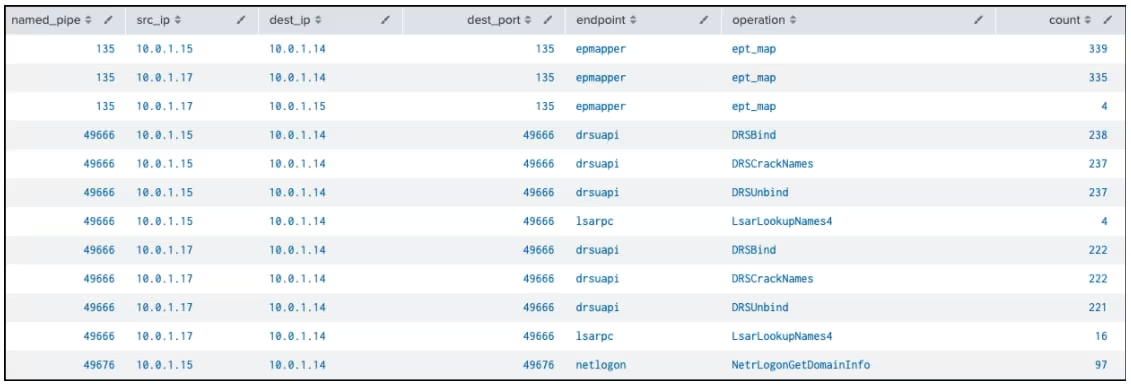
Zeek data can be used to identify named pipes used over RPC, and the stats command reveals source and destination IPs, ports, endpoints, and operations. For example, connections to named pipe 135 on port 135 (TCP) targeting the epmapper endpoint and performing the ept_map operation can be identified.
While these examples might seem common, they establish methods for investigating named pipes in your environment.
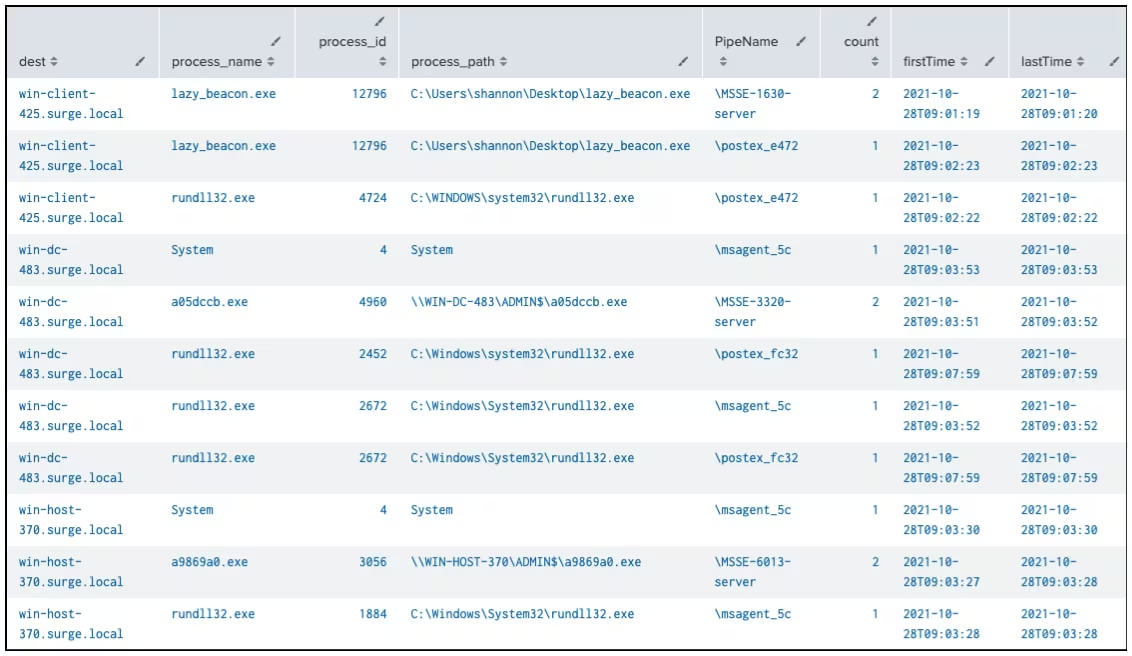
The researchers used Splunk Enterprise Security Content Update to find Cobalt Strike activity in a test environment, where the search focused on Sysmon events 17 and 18 that had to do with specific pipe names that Cobalt Strike often uses.
It was found that three Windows computers had been hacked: win-host-370.surge.local, win-dc-483.surge.local, and win-client-425.surge.local, while looking at the pipe names and processes showed that lateral movements (PSExec), SMB beaconing, and credential dumping (Mimikatz) were happening.
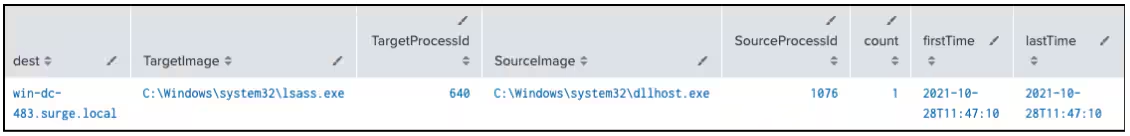
It has been investigated that hunting for Cobalt Strike Mimikatz activity by analyzing Sysmon EventCode 10 events targeting lsass.exe and looking for specific DLLs in the CallTrace field.
After identifying a suspicious dllhost.exe process with ProcessId 1076, the author pivoted to hunting for named pipes by analyzing Sysmon EventCode 17 and 18 events, which revealed the creation of a pipe named \Surgesock2\mrpipespostex-28b-0, which could be indicative of malicious lateral movement.
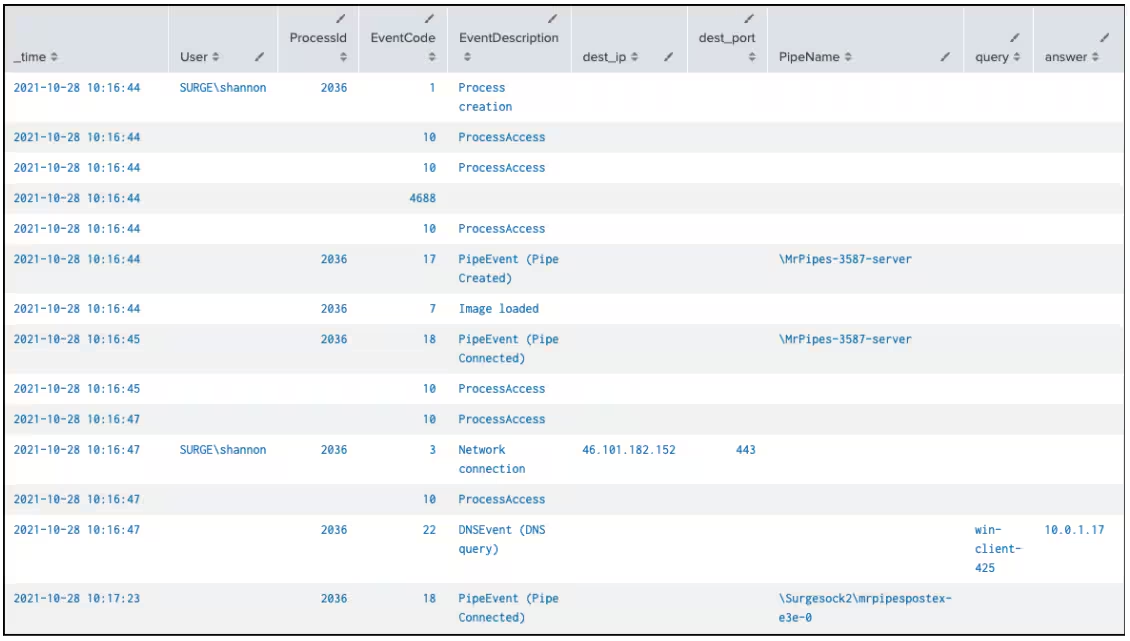
Then other suspicious pipe connections has been noted, including one using the UNC path WIN-DC-483 ADMIN$, which suggests potential SMB usage for file sharing.
An investigation into suspicious network activity identified a process named mr_pipes_surge.exe running on the Windows 10 client (WIN-CLIENT-425), which was not observed performing normal domain behavior like lsass.exe, and further analysis revealed the following:
- The user associated with the process was SURGE\shannon.
- The process made RPC calls to the domain controller (10.0.1.14) on port 135, which could be indicative of lateral movement using PSExec.
- The process communicated with an external IP address (46.101.182.152) on port 443, suggesting potential command and control communication.
- Pipes with names MrPipes-3587-server and \Surgesock2\mrpipespostex-e3e-0 were identified, potentially facilitating communication between processes.
The findings strongly suggest that mr_pipes_surge.exe may be a malicious process involved in lateral movement and communication with an external server.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!
Try Hack Me’s 1 Month Voucher Giveaway Link : https://forms.gle/xpqS2jgspyC22K5d8