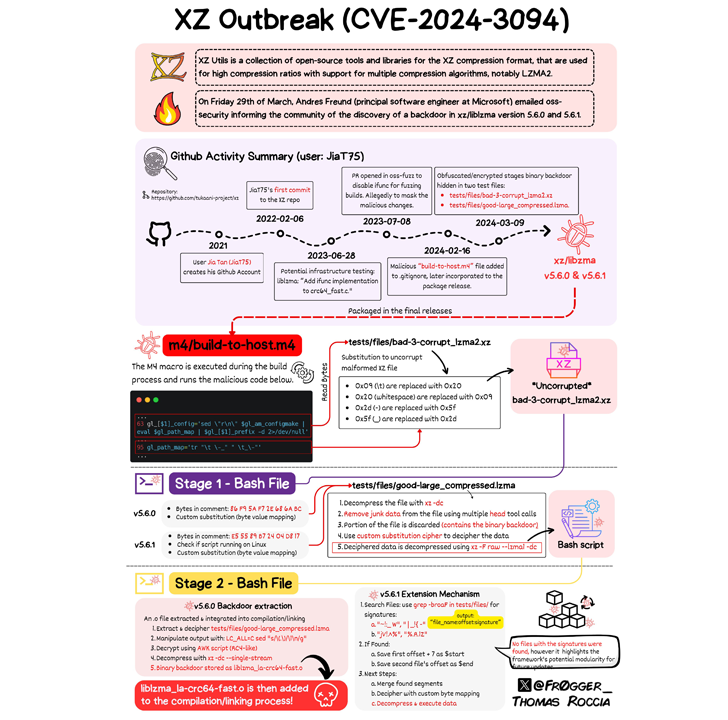
A critical supply chain vulnerability (CVE-2024-3094) has been discovered in XZ Utils (versions 5.6.0 and 5.6.1), a widely used open-source compression library, where malicious code injected into the source code exploits the liblzma build process to embed a pre-built object file.
The object file modifies liblzma functions, potentially enabling attackers to bypass SSH authentication and execute arbitrary commands on affected systems.
The vulnerability highlights the risk of unforeseen attacks within the open-source ecosystem and emphasizes the importance of vigilant supply chain management.
A malicious actor infiltrated the XZ project over the course of two years under the alias Jia Tan and by gradually contributing seemingly legitimate changes, they gained maintainer privileges.
The access was then exploited to embed a backdoor within a series of commits that were ultimately merged into XZ Utils versions 5.6.0 and 5.6.1, which likely reside within the compiled library, enabling potential remote code execution on affected systems.
An attacker named Jia Tan exploited social engineering to infiltrate the XZ project by creating fake accounts (Jigar Kumar, Dennis Ens) to bombard the maintainer with feature requests and bug reports.
The pressure campaign manipulated the maintainer (Lasse Collin) into granting Jia Tan co-maintainer privileges and then using their access to introduce a backdoor hidden within compressed test files.
The backdoor, most likely implemented through modifications to the configure script within the tar files, gave the attacker unauthorized remote access.
An attacker can exploit a vulnerability in an SSH server to gain unauthorized access to a victim machine that resides within a specific software package, which allows attackers to embed malicious code within an SSH certificate.
The code bypasses authentication protocols and executes on the victim machine once the certificate is accepted, granting the attacker full control as any internet-facing machine running the vulnerable software is at risk.
A sophisticated supply chain attack compromised XZ Utils, a widely used open-source compression utility for Linux, after the attacker spent two years infiltrating the project and earning trust by contributing to various open-source projects.
The malware specifically targeted Debian and RPM-based systems and could potentially grant unauthorized access under specific conditions, which highlights the importance of implementing tools and processes to continuously monitor for suspicious activity within open-source dependencies.
Analyzing Linux Vulnerabilities:
ANY.RUN provides an interactive cloud sandbox environment for malware analysis, allowing users to launch Ubuntu virtual machines and execute suspicious files, programs, or website links.
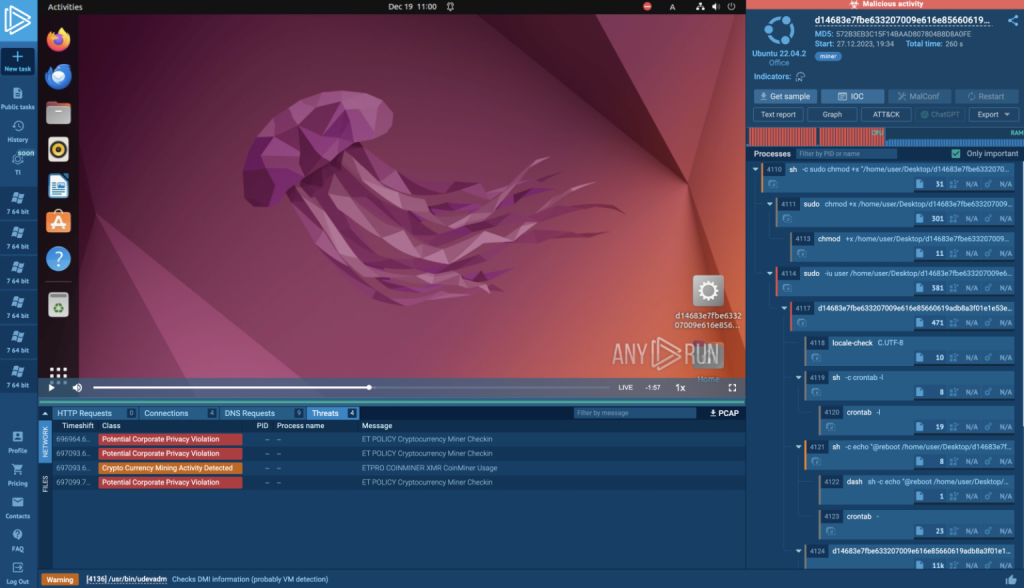
It emulates a real system’s behavior, enabling analysts to observe the malware’s execution and identify malicious activity, while the platform’s strength lies in its ability to detect threats through behavioral analysis, even for previously unknown malware strains.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!