A critical (CVSS score: 10.0) command injection vulnerability, CVE-2024-3400, has been found in Palo Alto Networks PAN-OS software’s GlobalProtect feature that allows remote attackers to execute malicious code with full administrative privileges on vulnerable firewalls, potentially compromising confidentiality, integrity, and availability of the device.
The vulnerability affects PAN-OS versions 10.2, 11.0, and 11.1 with specific configurations (GlobalProtect gateway/portal and device telemetry enabled), while patches are available, and users should apply them immediately.
The exploit requires specific PAN-OS versions and configurations, including the GlobalProtect gateway and device telemetry enabled, whereas Palo Alto Networks Cloud NGFW, Panorama, and Prisma Access are not susceptible to this vulnerability.
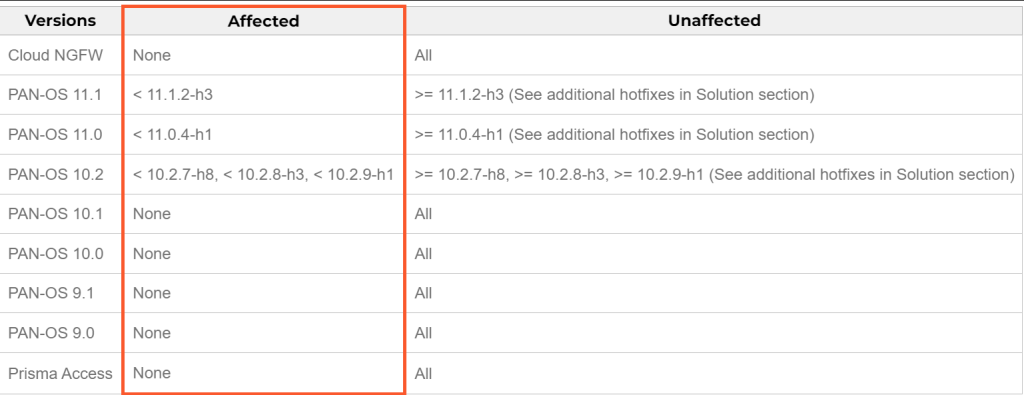
A critical vulnerability exists in certain Palo Alto Networks products where Cloud NGFW is not affected, but all PAN-OS versions below 11.1.2-h3, 11.0.4-h1, 10.2.7-h8, 10.2.8-h3, or 10.2.9-h1 are susceptible.
For PAN-OS 10.2, additional hotfixes may be necessary. PAN-OS versions 10.1, 10.0, 9.1, and 9.0 are not vulnerable and Prisma Access is also unaffected so upgrade to the aforementioned versions or apply the relevant hotfixes to address this issue.
Palo Alto Networks PAN-OS firewalls versions 10.2, 11.0, and 11.1 are susceptible to a critical command injection vulnerability (CVE-2024-3400) if they meet two conditions:
1) having either a GlobalProtect gateway or portal (or both) configured, and
2) having device telemetry enabled.
System administrators can check for these configurations within the firewall web interface: Network > GlobalProtect > Gateways/Portals for GlobalProtect presence and Device > Setup > Telemetry for device telemetry status.
The vulnerability allows attackers to remotely execute arbitrary commands with root privileges, potentially compromising the entire firewall. It exists due to the improper neutralization of special elements in user-controlled input.
The weakness, classified as CWE-77 (command injection), allows an attacker to inject arbitrary commands into an application that are then executed with the privileges of the application, whereas exploitation has been observed in the wild and a Palo Alto Networks Unit 42 threat brief provides additional details.
Solution for the vulnerability:
Palo Alto Networks released hotfixes to address a critical command injection vulnerability (CVE-2024-3400) in PAN-OS affecting GlobalProtect functionality, allowing unauthenticated attackers to execute arbitrary code with root privileges on the firewall.

PAN-OS versions 10.2.9-h1, 11.0.4-h1, and 11.1.2-h3 are patched as hotfixes for older versions are being released progressively. PAN-OS 10.2.6-h3 and 11.0.3-h10 are expected by April 16th, while all PAN-OS versions are expected to be addressed by April 19th.
Palo Alto Networks identified a critical OS command injection vulnerability (CVE-2024-3400) in PAN-OS GlobalProtect as they released patches on April 15th, 2024, and clarified workarounds for using Panorama templates to manage configurations.
The vulnerability potentially affects GlobalProtect portal configurations and customer-managed VMs in the cloud as more fixes are anticipated.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!
Try Hack Me’s 1 Month Voucher Giveaway Link : https://forms.gle/xpqS2jgspyC22K5d8