A vulnerability was found in Karrostech’s email verification process for their fleet management platform used by student transportation systems, allowing unauthorized access to potentially sensitive information, including student data (which may be for minors), school information, GPS data, and internal Karrostech information.
The vulnerability stemmed from two issues:
- 1) a bypass of the email verification process, and
- 2) the failure to revoke previously issued verification links.
This combination enabled attackers to gain access to accounts with email addresses they didn’t control, granting them privileges based on the associated domain (e.g., access to logging and monitoring utilities).
A critical vulnerability exists in Karrostech’s authentication infrastructure, as identified by advisory TRA-2024-11, where the details of the vulnerability are not publicly available, but the designation of “critical” risk factor suggests a severe potential exploit.
It could allow attackers to bypass authentication mechanisms and gain unauthorized access to protected systems or data. Users of Karrostech’s authentication infrastructure should immediately investigate this advisory and apply any available mitigations or updates.
A vulnerability in the Edulog Parent Portal’s email verification process allowed unauthorized access to Karrostech’s infrastructure and by exploiting the flaw, researchers bypassed email verification and gained access to the Keycloak instance managing Edulog accounts.
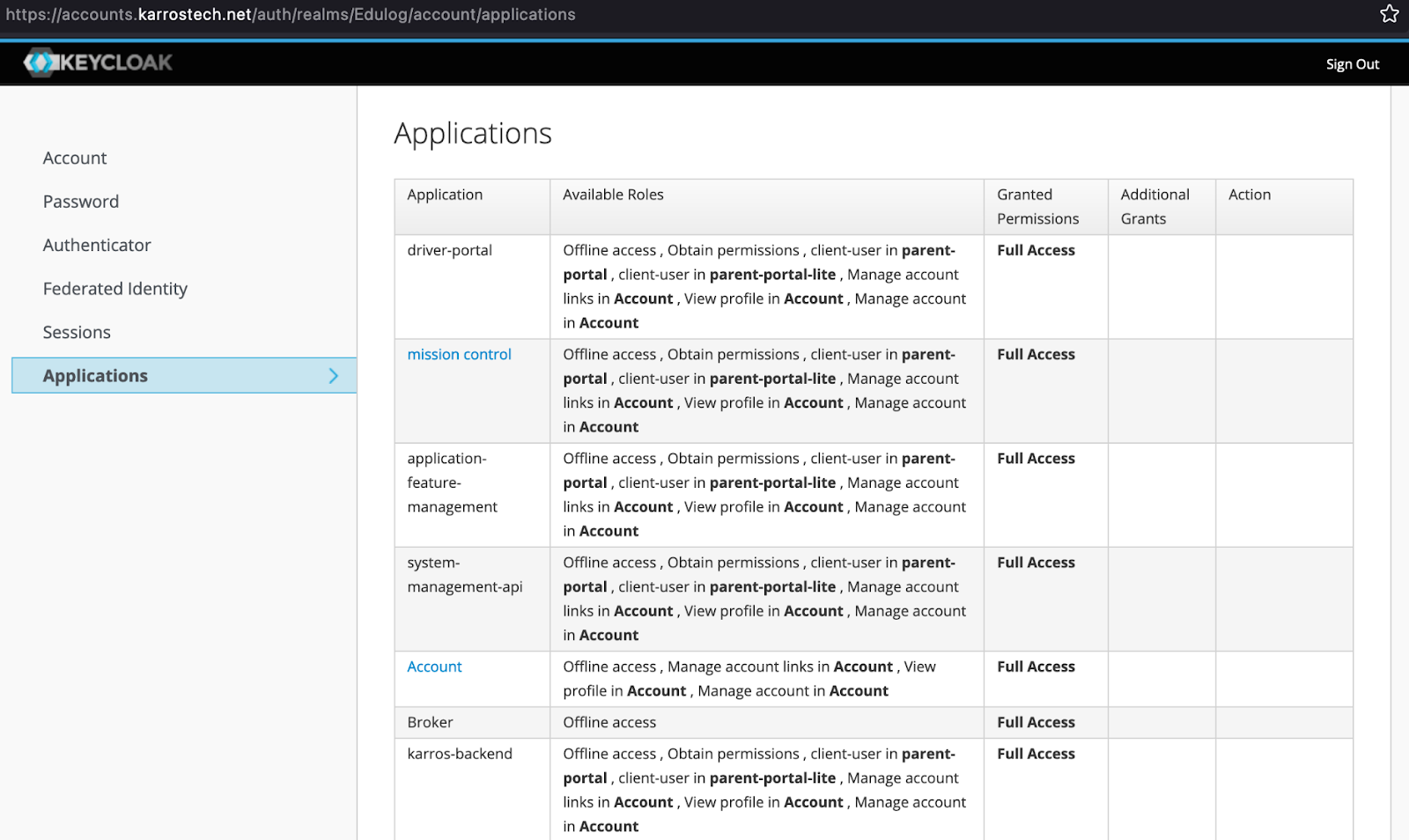
The misconfigured Keycloak allowed self-registration and granted access to the account management portal by default, which exposed sensitive data like student information (including GPS data for minors), internal Karrostech information, and customer details.
Researchers at Tenable discovered a vulnerability in a KeyCloak server configuration that allowed unauthorized access, as when a user changes their email and becomes unverified, their access tokens weren’t revoked and old verification links remained valid.
By manipulating these elements, researchers could create verified accounts with unauthorized email addresses (e.g., @karrostech.net), which granted access to restricted resources based on the email domain, including Karrostech’s logging and monitoring utilities containing sensitive data.
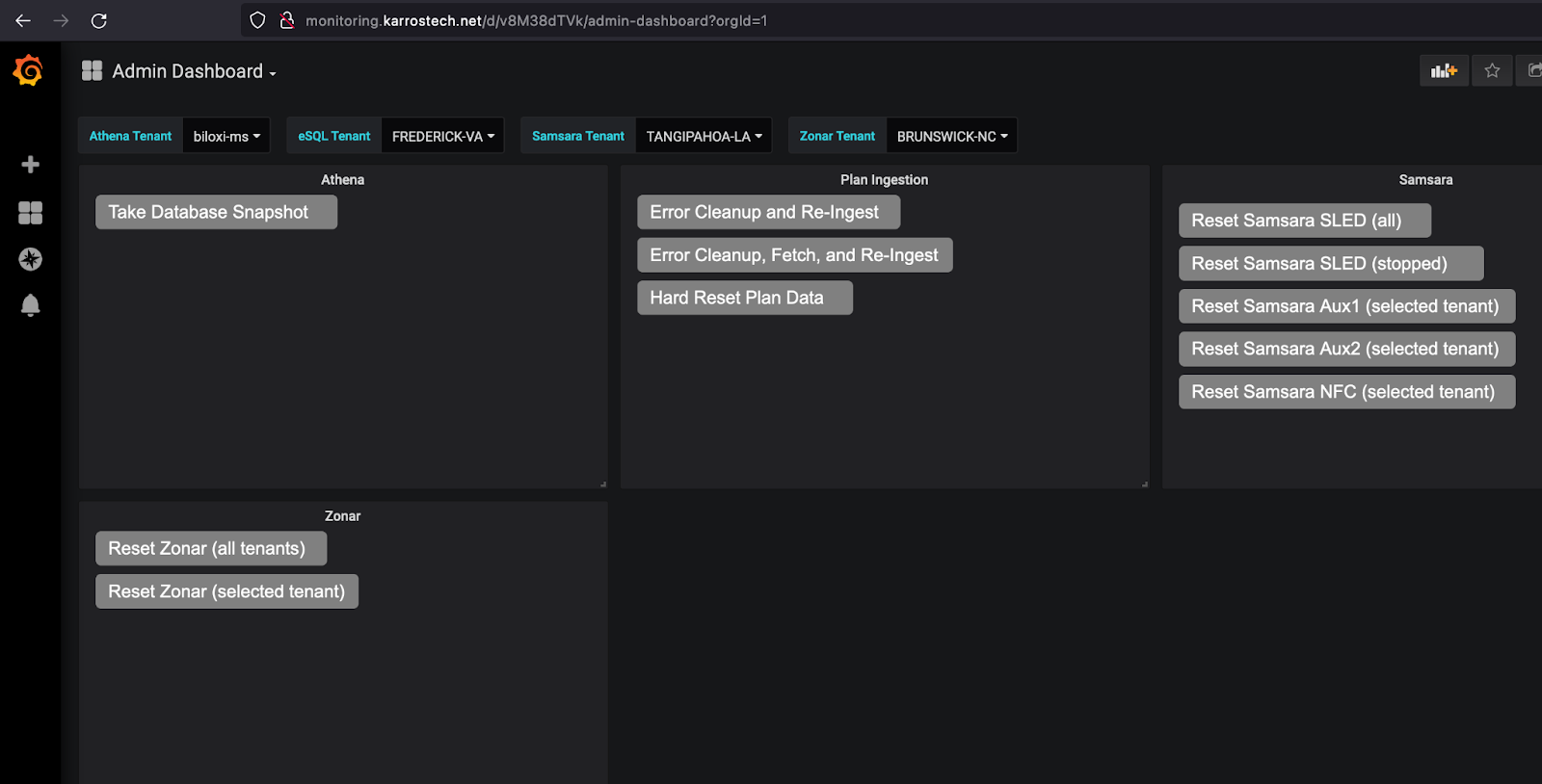
Karrostech identified and fixed security vulnerabilities in their cloud-based services by collaborating with a security researcher to disclose the details responsibly. The researcher attempted to contact Karrostech in December 2023, and disclosure happened in January 2024.
Throughout February and March, they followed up for updates and an unexpected public disclosure by a Karrostech customer on April 18th led to the researcher releasing their own advisory on April 19th, as both parties are currently working to clarify the information in their respective advisories.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!