Malware analysis activity increased 17.2% in Q1 2024 compared to Q4 2023, with nearly 877,000 public analysis sessions conducted. Of those analyzed, 17.8% were identified as malicious and 3.5% as suspicious, reflecting a slight decrease in overall malicious activity compared to the previous quarter.
The number of Indicators of Compromise (IOCs) that were collected by the researchers was greater than 238 million, with more than a quarter of them being ones that were not found anywhere else.
Top Malware Types in Q4 2023
The most common malware types identified by ANY.RUN’s sandbox are:
- Stealer: 5799
- RAT: 4956
- Loader: 4770
- Ransomware: 4065
- Keylogger: 1682
- Trojan: 972
- Backdoor: 587
- Miner: 277
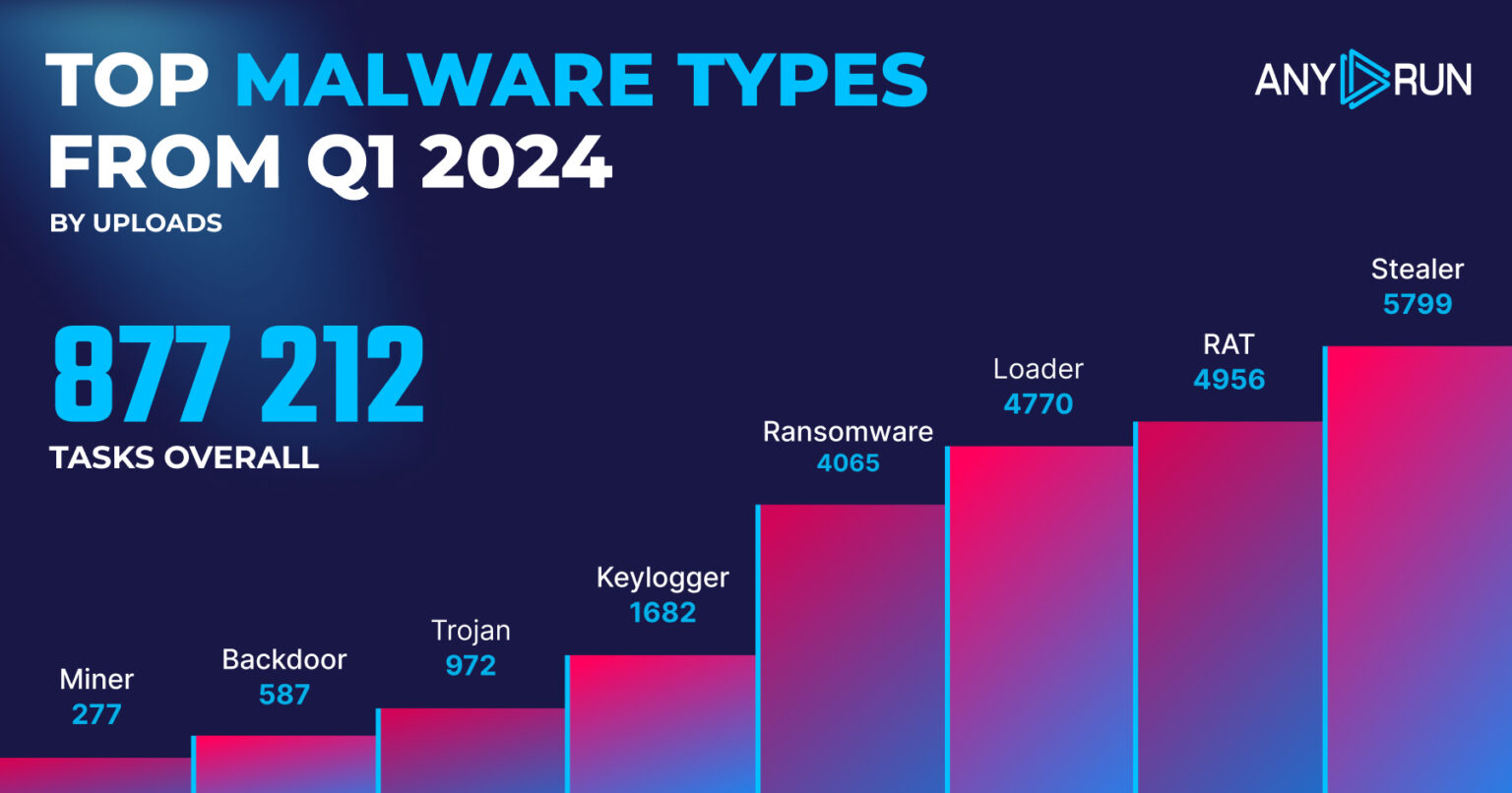
Analysis of malware detections in Q1 2024 reveals a shift in the threat landscape where stealer malware remains the most common type, but detections have decreased slightly.
RAT detections have surged, becoming the second most prevalent threat, while ransomware detections have also increased significantly but keylogger detections have doubled, indicating a rise in credential theft attempts.
Backdoor and miner detections haven’t changed substantially, which suggests a growing focus on stealing sensitive data and establishing persistent access within compromised systems.
Top Malware Families in Q1 2024
The malware families that have been used the most in the first quarter of 2024 are:
- Remcos: 1817
- Agent Tesla: 1739
- NjRAT: 1219
- AsyncRAT: 1155
- RedLine: 712
- Amadey: 400
- DCRat: 388
- Formbook: 359
- Emotet: 355
- Vidar: 227
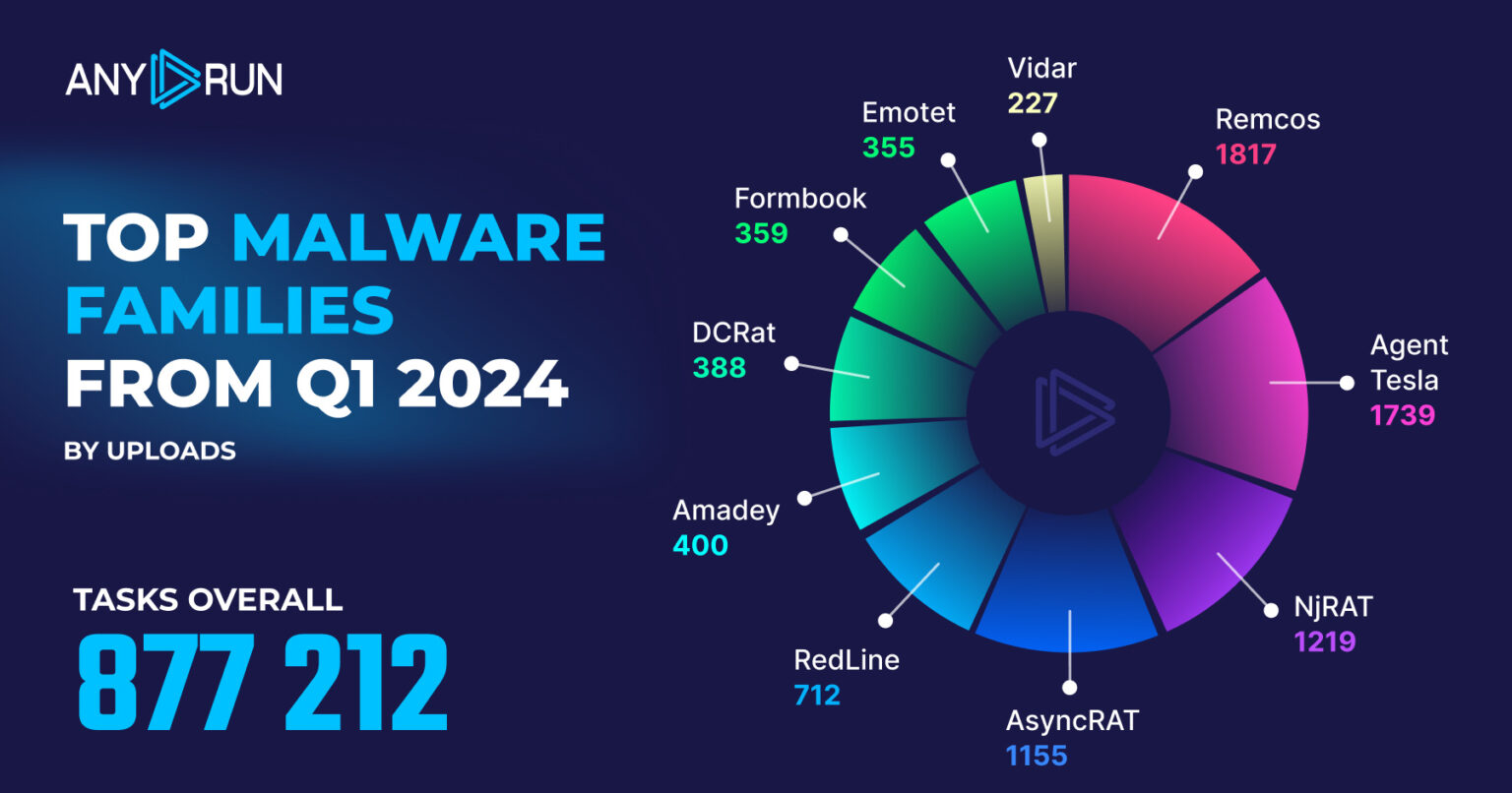
Q1 2024 saw a shift in the top malware families as Remcos surged to the top position with a substantial increase, while RedLine experienced a significant decline but Agent Tesla remained prevalent but dropped to second place.
Newcomers like NjRAT and DCRat emerged in the top rankings, while established threats like AsyncRAT saw a sharp rise, indicating a dynamic malware landscape with evolving dominance among Remote Access Trojans (RATs) and information stealers.
Top MITRE ATT&CK techniques in Q1 2024
Malware analysts can use the MITRE ATT&CK framework to prioritize threat detection efforts, where techniques like email collection and exploitation of legitimate tools (Rundll32) are highly prevalent, with tens of thousands of detections each.
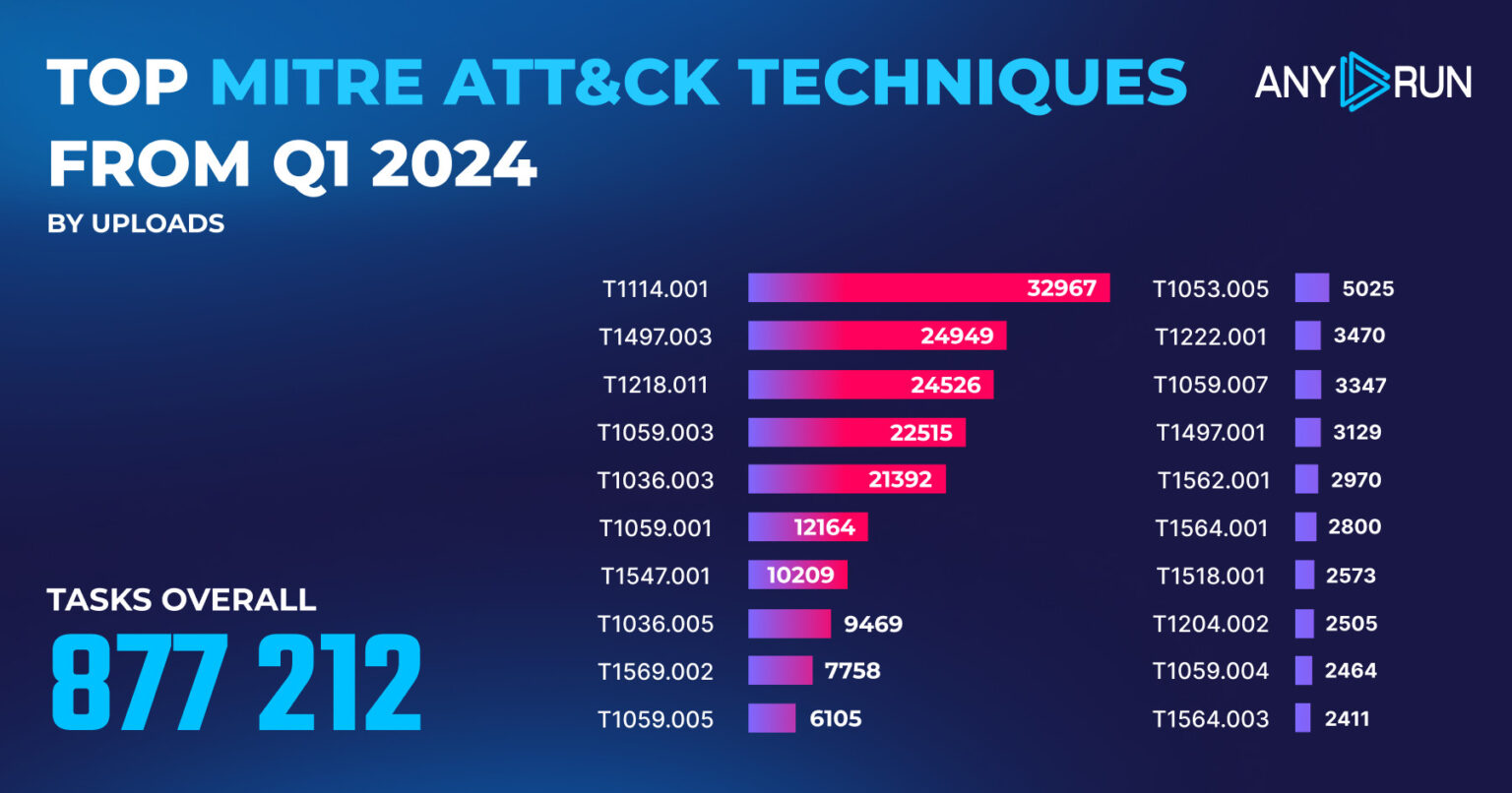
Abusing PowerShell scripting and exploiting autoruns (Registry Run Keys) are also common, where tactics for evasion (time-based and system checks) and maintaining persistence (hidden files and scheduled tasks) are frequently observed. Analysts should prioritize detection mechanisms for these techniques to effectively mitigate adversary actions.
Adversary tactics shifted significantly between Q4 2023 and Q1 2024. Masquerading with legitimate names or locations (T1036.005) saw a dramatic decline (90.4%), while techniques like local email collection (T1114.001) surged to the top spot (21% increase).
Time-based evasion for virtualization/sandbox environments (T1497.003) tripled detections, jumping to second place, while Rundll32 proxy execution (T1218.011) also gained traction (a 14.5% increase).
The findings suggest a move away from basic impersonation tactics and a rise in techniques that exploit email collection opportunities and time-based manipulation to bypass security controls.
Never forget to check out our YouTube channel, ETHICAL EMPIRE, and keep reading our exciting blogs. Until next time, stay curious, stay secure, and keep exploring the fascinating world of cyber security. See you soon, bye!
Try Hack Me’s 1 Month Voucher Giveaway Link : https://forms.gle/xpqS2jgspyC22K5d8